
Introduction & Overview
What is OWASP ZAP?
OWASP ZAP (Zed Attack Proxy) is an open-source, free-to-use web application security testing tool maintained by the Open Web Application Security Project (OWASP). It is designed to identify vulnerabilities in web applications during development, testing, and deployment phases. ZAP acts as an intercepting proxy, capturing HTTP/HTTPS traffic between a browser and a web application to analyze and test for security flaws such as SQL injection, cross-site scripting (XSS), and broken authentication. Its versatility makes it suitable for both beginners and experienced security professionals.
History or Background
OWASP ZAP was founded in 2010 by Simon Bennetts under the OWASP umbrella, a non-profit organization established in 2001 to enhance software security. ZAP has evolved into one of the most widely used security scanners, with over 100,000 monthly downloads. Its open-source nature and active community contributions have driven continuous updates, ensuring compatibility with modern web technologies like WebSockets and APIs. ZAP’s plugin architecture and marketplace have further expanded its capabilities, making it a staple in security testing.
Why is it Relevant in DevSecOps?
DevSecOps integrates security into every phase of the software development lifecycle (SDLC), emphasizing automation and continuous security validation. OWASP ZAP aligns with this philosophy by:
- Automating Security Testing: ZAP’s automated scanning capabilities allow teams to detect vulnerabilities early in the CI/CD pipeline, reducing the risk of deploying insecure code.
- Shift-Left Security: ZAP enables developers to identify and fix issues during development, fostering a security-first mindset.
- Compliance Support: ZAP helps address OWASP Top 10 vulnerabilities, a key requirement for compliance frameworks like SOC II.
- Open-Source Accessibility: Being free and community-driven, ZAP lowers the barrier for organizations to adopt robust security practices.
Core Concepts & Terminology
Key Terms and Definitions
- Proxy: ZAP acts as a man-in-the-middle, intercepting and analyzing HTTP/HTTPS traffic between the browser and the target application.
- Passive Scanning: Non-intrusive analysis of requests and responses to identify vulnerabilities without modifying traffic.
- Active Scanning: Actively sends payloads to test for vulnerabilities, simulating real attacks (requires permission to avoid legal issues).
- Spidering: Crawls a web application to map its structure, identifying links, pages, and endpoints.
- AJAX Spider: An add-on for crawling JavaScript-heavy applications, such as single-page applications (SPAs).
- Fuzzing: Sends unexpected or malformed inputs to test application resilience.
- Context: A defined scope of URLs or applications for targeted scanning.
- Alerts: Notifications of potential vulnerabilities, categorized by severity (High, Medium, Low).
| Term | Description |
| -------------------- | ----------------------------------------------------------------- |
| DAST | Dynamic Application Security Testing – testing apps while running |
| Passive Scanning | Observes traffic without impacting target |
| Active Scanning | Sends potentially malicious requests to find vulnerabilities |
| Spidering | Crawling the application to discover pages and endpoints |
| ZAP API | REST-based API to control ZAP from scripts or CI tools |
How It Fits into the DevSecOps Lifecycle
ZAP integrates into the DevSecOps pipeline across multiple phases:
- Plan: Define security requirements and configure ZAP scan policies to target specific vulnerabilities.
- Code: Use ZAP for manual testing during development to catch issues early.
- Build: Integrate ZAP into CI/CD pipelines (e.g., Jenkins, GitHub Actions) for automated scans on code commits.
- Test: Perform active and passive scans to validate application security in staging environments.
- Deploy: Ensure vulnerabilities are addressed before production deployment.
- Monitor: Run periodic scans to detect new vulnerabilities post-deployment.
Architecture & How It Works
Components and Internal Workflow
ZAP’s architecture is modular, comprising:
- Proxy Server: Captures and inspects HTTP/HTTPS traffic, enabling analysis of requests and responses.
- Scanner: Performs passive and active scans to identify vulnerabilities like XSS, SQL injection, and misconfigurations.
- Spider: Crawls applications to build a sitemap, with traditional and AJAX spiders for different application types.
- Fuzzer: Tests applications with unexpected inputs to uncover weaknesses.
- API: Facilitates automation and integration with CI/CD tools, supporting JSON, XML, and HTML formats.
- User Interface: Offers a GUI for interactive testing and a CLI for automation.
- Database: Stores session data, including requests, responses, and alerts.
Workflow:
- ZAP intercepts traffic as a proxy between the browser and the application.
- The spider crawls the application to map its structure.
- Passive scans analyze traffic for vulnerabilities without altering it.
- Active scans send payloads to test for exploitable flaws.
- Results are displayed in the Alerts tab, categorized by severity, with detailed reports generated in formats like HTML or JSON.
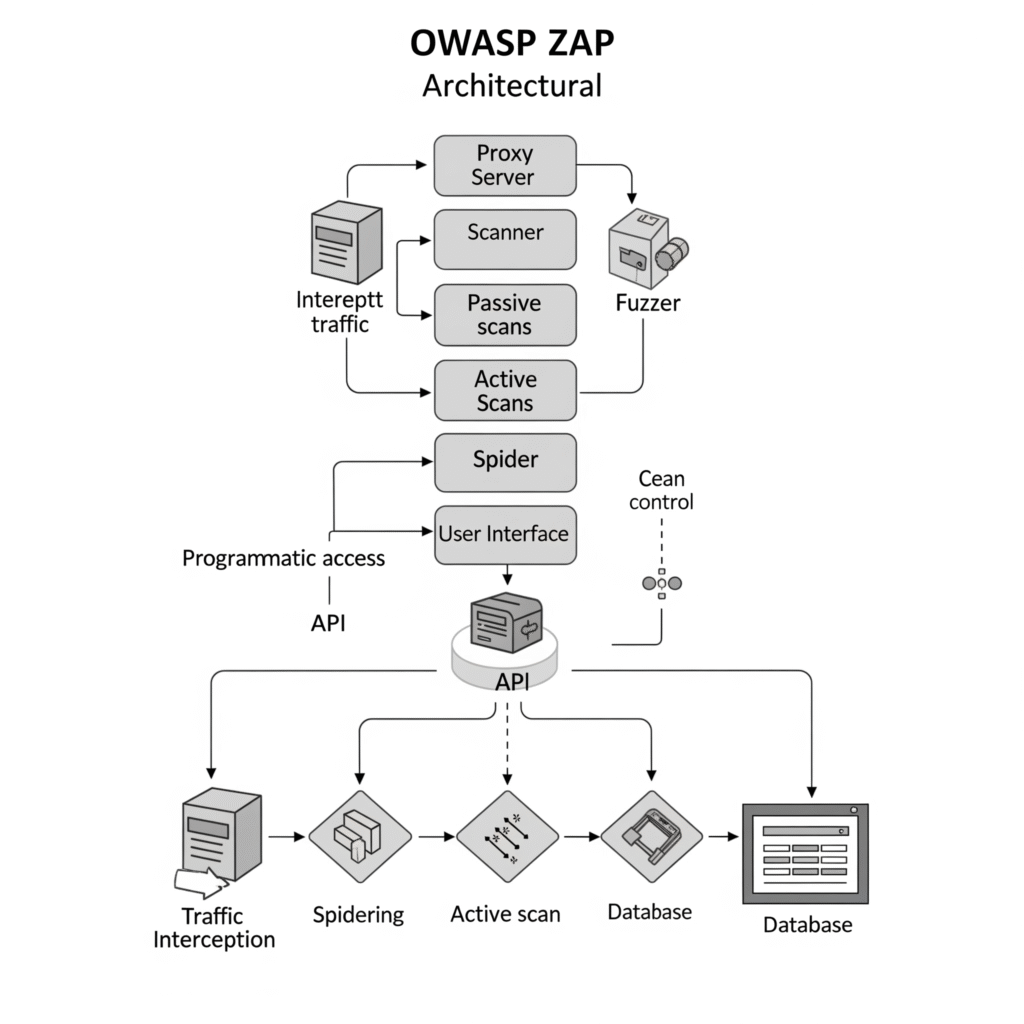
Architecture Diagram
Due to text-based limitations, imagine a diagram with:
- A browser at the left, sending HTTP/HTTPS requests.
- ZAP in the center, with modules (Proxy, Scanner, Spider, Fuzzer, API) interconnected.
- A web application on the right, receiving requests and sending responses.
- Arrows showing bidirectional traffic flow through ZAP, with data stored in a local database.
- CI/CD tools (e.g., Jenkins) interacting with ZAP via its API.
[Developer/CI/CD] ---> [ZAP Proxy]
|
+----------+----------+
| |
[Spider] [Scanner]
| |
[Active/Passive] [Results]
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: ZAP’s API and CLI enable seamless integration with Jenkins, GitHub Actions, or GitLab CI. For example, a Jenkins pipeline can trigger ZAP scans post-build and fail the pipeline if critical vulnerabilities are found.
- Cloud Compatibility: ZAP runs in Docker containers, making it suitable for cloud-based CI/CD environments like AWS CodePipeline or Azure DevOps.
- Reporting: ZAP integrates with SIEM systems or ticketing tools (e.g., Jira) to streamline vulnerability management.
Installation & Getting Started
Basic Setup and Prerequisites
- Operating System: Windows, macOS, or Linux.
- Java: Java 11+ (required for Windows/Linux; included in macOS installer).
- Browser: Firefox or Chrome for proxy setup.
- Network: Access to the target application and permission to scan.
- Disk Space: ~500 MB for installation and session data.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
- Download ZAP:
- Visit https://www.zaproxy.org/download/ and download the installer for your OS.
- For Docker:
docker pull owasp/zap2docker-stable- Install ZAP:
- Run the installer and follow prompts. Accept the license agreement.
- For Docker:
Run docker run -u zap -p 8080:8080 -i owasp/zap2docker-stable zap.sh -daemon.- Configure Proxy:
- Open ZAP, go to Tools > Options > Local Proxy, and note the default settings (localhost:8080).
- In Firefox: Go to Preferences > Network Settings > Manual Proxy Configuration, set HTTP Proxy to
localhostand Port to8080.
- Install ZAP Certificate:
- In ZAP, go to Tools > Options > Dynamic SSL Certificates, and export the certificate.
- In Firefox: Go to Preferences > Privacy & Security > Certificates > View Certificates > Import, and select the exported certificate.
- Run a Quick Scan:
- Open ZAP’s Quick Start tab.
- Enter the target URL (e.g.,
http://example.com). - Select Automated Scan and click Attack.
- ZAP will crawl the site and perform passive/active scans, displaying results in the Alerts tab.
- Generate a Report:
- Go to Report > Generate HTML Report, specify a file path, and save the report.
Real-World Use Cases
- Automated Vulnerability Scanning in CI/CD:
- Scenario: A fintech company integrates ZAP into its Jenkins pipeline to scan a payment processing application.
- Implementation: A Jenkins job triggers ZAP’s API to run an active scan after each build. If high-severity alerts (e.g., SQL injection) are detected, the pipeline fails, alerting developers via Slack.
- Outcome: Vulnerabilities are caught before deployment, ensuring compliance with PCI-DSS.
- API Security Testing:
- Scenario: A healthcare provider tests REST APIs for a patient portal.
- Implementation: ZAP’s API scanning capabilities are used to test endpoints for issues like insecure deserialization. Authentication is configured for JWT-based APIs.
- Outcome: Identifies missing security headers, enabling fixes before patient data exposure.
- Single-Page Application (SPA) Testing:
- Scenario: An e-commerce platform uses ZAP to test a JavaScript-heavy SPA.
- Implementation: The AJAX Spider is enabled to crawl dynamic routes, followed by active scanning for XSS vulnerabilities.
- Outcome: Uncovers client-side vulnerabilities, improving customer data protection.
- WebSocket Security Testing:
Benefits & Limitations
Key Advantages
- Cost-Effective: Free and open-source, with no licensing fees.
- Comprehensive Features: Supports passive/active scanning, fuzzing, spidering, and WebSocket testing.
- Extensibility: Marketplace add-ons enhance functionality (e.g., AJAX Spider, custom scripts).
- Community Support: Active forums and documentation provide robust resources.
- CI/CD Integration: Seamlessly integrates with DevSecOps pipelines.

Common Challenges or Limitations
- False Positives/Negatives: Automated scans may flag non-issues or miss complex vulnerabilities, requiring manual verification.
- Resource Intensity: Active scans can strain low-capacity environments; optimization is needed.
- Learning Curve: Novice users may find the UI and configuration complex.
- Limited Logic Testing: Cannot detect application logic errors, which require manual audits.
Best Practices & Recommendations
- Security Tips:
- Always obtain permission before active scanning to avoid legal issues.
- Use context-specific configurations to focus scans on relevant URLs.
- Combine passive and active scans for comprehensive coverage.
- Performance:
- Adjust scan policies to limit request frequency and avoid overwhelming the target application.
- Use headless mode or Docker for resource-efficient CI/CD scans.
- Maintenance:
- Regularly update ZAP and its add-ons to leverage the latest vulnerability checks.
- Review and fine-tune scan policies to reduce false positives.
- Compliance Alignment:
- Map scan results to OWASP Top 10 for compliance reporting (e.g., SOC II, PCI-DSS).
- Generate detailed HTML reports for audit trails.
- Automation Ideas:
- Integrate ZAP with GitHub Actions using a script like:
docker run -v $(pwd):/zap/wrk/:rw -t owasp/zap2docker-stable zap-api-scan.py -t https://example.com -f openapi -r report.htmlComparison with Alternatives
| Feature | OWASP ZAP | Burp Suite | Acunetix |
|---|---|---|---|
| Cost | Free, open-source | Freemium (paid Pro/Enterprise editions) | Paid (subscription-based) |
| Ease of Use | Moderate (GUI/CLI, some learning curve) | Moderate (complex for beginners) | High (user-friendly, web-based) |
| Automation | Strong (API, CI/CD integration) | Strong (API, scripting support) | Strong (CI/CD, scheduled scans) |
| Features | Scanning, fuzzing, spidering, WebSockets | Advanced manual testing, extensibility | Broad vulnerability coverage, compliance |
| Community Support | Strong (OWASP community, forums) | Moderate (commercial support for Pro) | Commercial support only |
| Best For | DevSecOps, budget-conscious teams | Advanced pen-testers | Enterprises with compliance needs |
When to Choose OWASP ZAP:
- Budget constraints or open-source preference.
- Need for CI/CD integration and automation.
- Testing modern web technologies (e.g., APIs, WebSockets).
- Community-driven support and extensibility are priorities.
Choose Alternatives:
- Burp Suite: For advanced manual penetration testing or when premium features are needed.
- Acunetix: For enterprises requiring polished UI and compliance-focused reporting.
Conclusion
OWASP ZAP is a powerful, accessible tool for integrating security into DevSecOps workflows. Its automation capabilities, extensibility, and alignment with OWASP Top 10 make it ideal for catching vulnerabilities early and ensuring compliance. While it has limitations like false positives and resource intensity, proper configuration and best practices mitigate these challenges. As DevSecOps adoption grows, ZAP’s role in fostering a security-first culture will expand, especially with ongoing updates supporting emerging technologies.