Introduction & Overview
Penetration testing, often referred to as “pen testing,” is a critical practice in cybersecurity that involves simulating cyberattacks to identify vulnerabilities in systems, applications, or networks. In the DevSecOps framework, where security is integrated into the development and operations lifecycle, penetration testing plays a pivotal role in ensuring robust security postures. This tutorial provides an in-depth exploration of penetration testing within DevSecOps, covering its concepts, integration, setup, use cases, benefits, limitations, and best practices.
What is Penetration Testing?
Penetration testing is a controlled process where security professionals, or “ethical hackers,” attempt to exploit vulnerabilities in a system to assess its security. The goal is to identify weaknesses before malicious actors can exploit them.
- Key Objectives:
- Identify vulnerabilities in code, configurations, or infrastructure.
- Validate security controls and compliance requirements.
- Provide actionable remediation recommendations.
History or Background
Penetration testing emerged in the 1960s when early computer systems faced increasing risks from unauthorized access. The term gained prominence in the 1990s with the rise of the internet and formalized methodologies like the Open Source Security Testing Methodology Manual (OSSTMM) and Penetration Testing Execution Standard (PTES). In DevSecOps, penetration testing has evolved to align with agile and continuous delivery practices, ensuring security keeps pace with rapid development cycles.
Why is it Relevant in DevSecOps?
DevSecOps integrates security into every phase of the software development lifecycle (SDLC), emphasizing “shift-left” security. Penetration testing complements this by:
- Proactive Risk Mitigation: Identifies vulnerabilities early in development or deployment.
- Continuous Security: Aligns with CI/CD pipelines for ongoing testing.
- Compliance and Trust: Ensures adherence to standards like PCI-DSS, HIPAA, or GDPR, building customer confidence.
Core Concepts & Terminology
Key Terms and Definitions
- Vulnerability: A weakness in a system that can be exploited.
- Exploit: A method or tool used to take advantage of a vulnerability.
- Penetration Test Types:
- Black Box: Tester has no prior knowledge of the system.
- White Box: Tester has full knowledge of the system architecture.
- Gray Box: Partial knowledge is provided to the tester.
- Attack Vector: The path or method used to exploit a system (e.g., network, application, social engineering).
- Threat Modeling: Identifying potential threats to prioritize testing efforts.
- Red Team/Blue Team: Red team simulates attackers, while blue team defends the system.
How It Fits into the DevSecOps Lifecycle
Penetration testing integrates into the DevSecOps lifecycle at multiple stages:
- Plan: Identify assets and define test scope using threat modeling.
- Code: Test code for vulnerabilities (e.g., SQL injection, XSS).
- Build: Scan dependencies and configurations in CI pipelines.
- Test: Conduct automated and manual pen tests before deployment.
- Deploy: Validate production environments for misconfigurations.
- Monitor: Perform periodic tests to detect new vulnerabilities.
Architecture & How It Works
Components and Internal Workflow
Penetration testing in DevSecOps involves several components:
- Reconnaissance Tools: Gather information (e.g., Nmap for network scanning, Shodan for internet-exposed devices).
- Vulnerability Scanners: Identify known vulnerabilities (e.g., Nessus, OWASP ZAP).
- Exploitation Frameworks: Execute exploits (e.g., Metasploit, Burp Suite).
- Reporting Tools: Generate detailed reports for remediation (e.g., Dradis).
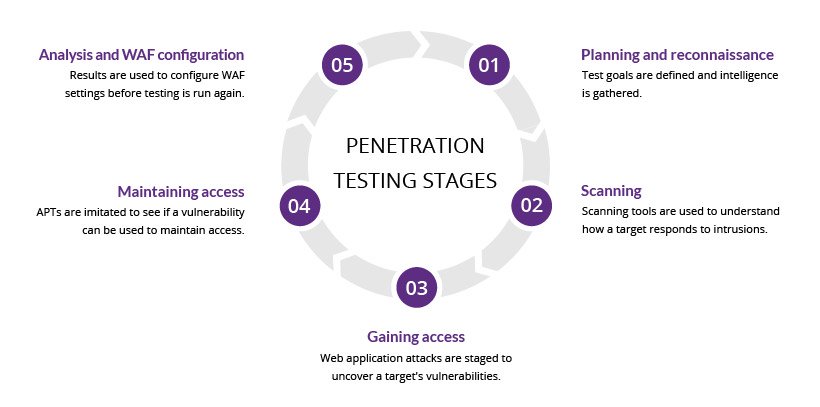
Workflow:
- Planning and Scoping: Define objectives, targets, and rules of engagement.
- Reconnaissance: Collect data on the target system (e.g., IP ranges, open ports).
- Scanning: Identify vulnerabilities using automated tools.
- Exploitation: Attempt to exploit vulnerabilities to assess impact.
- Post-Exploitation: Document findings, including data accessed or systems compromised.
- Reporting: Provide detailed reports with remediation steps.
Architecture Diagram (Text Description)
Imagine a flowchart with the following components:
- CI/CD Pipeline: Central horizontal line representing code commit to deployment.
- Penetration Testing Layer: A parallel layer interacting at key stages (Code, Build, Test, Deploy).
- Tools: Boxes labeled “Nmap,” “Metasploit,” “OWASP ZAP,” connected to the testing layer.
- Feedback Loop: Arrows from testing results back to development for remediation.
- Cloud Integration: A cloud icon (e.g., AWS/GCP) linked to deployment and monitoring stages.
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration:
- Embed vulnerability scans in Jenkins or GitLab CI pipelines using tools like OWASP Dependency-Check.
- Automate pen tests with scripts triggered post-build.
- Cloud Tools:
- Use AWS Inspector or Azure Security Center for cloud-native vulnerability assessments.
- Integrate with Kubernetes for container security testing (e.g., kube-hunter).
Installation & Getting Started
Basic Setup or Prerequisites
To set up a penetration testing environment for DevSecOps:
- Hardware: A system with 8GB RAM, 4-core CPU, and 50GB storage.
- Operating System: Kali Linux or Parrot Security OS (preferred for pre-installed tools).
- Software:
- Nmap, Metasploit, Burp Suite, OWASP ZAP.
- Docker for containerized testing environments.
- Git for version control integration.
- Permissions: Ensure legal authorization for testing target systems.
- Network Access: Stable internet and access to target environments (e.g., staging servers).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide sets up a basic penetration testing environment using Kali Linux and OWASP ZAP in a DevSecOps pipeline.
- Install Kali Linux:
- Download the Kali Linux ISO from
https://www.kali.org/. - Create a bootable USB or install in a VM (e.g., VirtualBox).
- Boot and follow the installation wizard.
- Download the Kali Linux ISO from
- Install OWASP ZAP:
sudo apt update sudo apt install zaproxy3. Set Up a Test Application:
- Clone a vulnerable web app for testing (e.g., Damn Vulnerable Web Application – DVWA):
git clone https://github.com/digininja/DVWA.git
cd DVWA
docker-compose up4. Configure OWASP ZAP in CI/CD (e.g., Jenkins):
- Install Jenkins on your system:
sudo apt install openjdk-11-jdk
wget -q -O - https://pkg.jenkins.io/debian/jenkins.io.key | sudo apt-key add -
sudo sh -c 'echo deb http://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list'
sudo apt update
sudo apt install jenkins- Create a Jenkins pipeline to run OWASP ZAP:
pipeline {
agent any
stages {
stage('Run OWASP ZAP') {
steps {
sh 'zap-cli start --start-options "-config api.key=your-api-key"'
sh 'zap-cli spider http://localhost:8080'
sh 'zap-cli active-scan http://localhost:8080'
sh 'zap-cli report -o zap-report.html -f html'
}
}
}
}5. Run a Test:
- Access OWASP ZAP GUI:
zap.sh -port 8090. - Configure the target URL (e.g.,
http://localhost:8080for DVWA). - Start a spider scan and active scan to identify vulnerabilities.
- Export the report for review.
Real-World Use Cases
Scenario 1: E-Commerce Platform Security
An e-commerce company integrates penetration testing into its DevSecOps pipeline to secure customer data.
- Implementation: Automated OWASP ZAP scans in CI/CD detect SQL injection vulnerabilities in the checkout process.
- Outcome: Fixes vulnerabilities before deployment, ensuring PCI-DSS compliance.
Scenario 2: Healthcare Application Compliance
A healthcare provider uses penetration testing to meet HIPAA requirements.
- Implementation: Manual white-box testing with Burp Suite identifies weak encryption in patient data APIs.
- Outcome: Strengthens encryption, preventing data breaches.
Scenario 3: Cloud-Native Microservices
A fintech startup tests its Kubernetes-based microservices.
- Implementation: Kube-hunter scans for misconfigured pods, followed by Metasploit exploitation tests.
- Outcome: Secures container environments, reducing attack surfaces.
Industry-Specific Example: Finance
Banks use penetration testing to secure online banking platforms, focusing on vulnerabilities like session hijacking or XSS, ensuring compliance with regulations like SOX.
Benefits & Limitations
Key Advantages
- Proactive Security: Identifies vulnerabilities before exploitation.
- Compliance Alignment: Meets standards like GDPR, PCI-DSS, and HIPAA.
- Improved Code Quality: Encourages secure coding practices in DevSecOps.
- Customer Trust: Demonstrates commitment to security.
Common Challenges or Limitations
- Scope Limitations: Tests may miss zero-day vulnerabilities.
- Resource Intensive: Manual testing requires skilled professionals.
- False Positives: Automated tools may report non-issues, requiring validation.
- Dynamic Environments: Cloud and microservices complexity can complicate testing.
Best Practices & Recommendations
- Automate Where Possible: Integrate tools like OWASP ZAP or Nessus into CI/CD pipelines.
- Regular Testing: Schedule periodic manual and automated tests.
- Threat Modeling: Prioritize high-risk assets for focused testing.
- Compliance Alignment: Map tests to regulatory requirements (e.g., OWASP Top 10 for web apps).
- Team Training: Educate developers on secure coding to reduce vulnerabilities.
- Tool Maintenance: Keep tools updated to detect new vulnerabilities.
Comparison with Alternatives
| Aspect | Penetration Testing | Static Application Security Testing (SAST) | Dynamic Application Security Testing (DAST) |
|---|---|---|---|
| Approach | Simulates real-world attacks | Analyzes source code without execution | Tests running applications |
| Strengths | Realistic, identifies exploitable issues | Early detection in code | Tests runtime behavior |
| Weaknesses | Resource-intensive, may miss zero-days | Limited to code, misses runtime issues | Misses code-level issues |
| Best Use Case | Comprehensive security validation | Early SDLC vulnerability detection | Runtime vulnerability scanning |
When to Choose Penetration Testing:
- Use for high-stakes applications requiring thorough validation.
- Prefer over SAST/DAST when simulating real attacker behavior is critical.
Conclusion
Penetration testing is a cornerstone of DevSecOps, enabling organizations to proactively secure their systems while aligning with agile development practices. By integrating testing into CI/CD pipelines and leveraging tools like OWASP ZAP and Metasploit, teams can maintain robust security postures. Future trends include AI-driven testing and increased automation for real-time vulnerability detection.
Next Steps:
- Explore tools like Kali Linux and OWASP ZAP.
1 thought on “Penetration Testing in the Context of DevSecOps: A Comprehensive Tutorial”