Introduction & Overview
Threat modeling is a structured approach to identifying, assessing, and mitigating security risks in software systems. In DevSecOps, it integrates security into the development and operations lifecycle, ensuring that security is a shared responsibility across teams. This tutorial provides an in-depth guide to threat modeling, tailored for DevSecOps practitioners, covering its concepts, implementation, use cases, and best practices.

What is Threat Modeling?
Threat modeling is a proactive security process that identifies potential threats to a system, evaluates their impact, and defines mitigation strategies. It helps teams understand the attack surface of their applications and prioritize security efforts.

History or Background
Threat modeling emerged in the late 1990s, with Microsoft’s STRIDE model (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) as a foundational framework. Over time, methodologies like DREAD, PASTA, and OWASP’s Threat Dragon have evolved, adapting to modern development practices like DevSecOps.
Why is it Relevant in DevSecOps?
In DevSecOps, security is embedded into every phase of the software development lifecycle (SDLC). Threat modeling aligns with this by:
- Enabling early identification of vulnerabilities during design and development.
- Fostering collaboration between development, security, and operations teams.
- Supporting compliance with standards like GDPR, HIPAA, and PCI-DSS.
- Reducing costs by addressing security issues before deployment.
Core Concepts & Terminology
Key Terms and Definitions
- Threat: A potential event that could harm the system (e.g., data breach).
- Vulnerability: A weakness that a threat could exploit.
- Attack Surface: All entry points where an attacker could interact with the system.
- Mitigation: Actions to reduce the likelihood or impact of a threat.
- STRIDE: A Microsoft framework for categorizing threats (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege).
- Data Flow Diagram (DFD): A visual representation of data movement within a system.
How it Fits into the DevSecOps Lifecycle
Threat modeling integrates into DevSecOps at multiple stages:
- Plan: Identify security requirements during sprint planning.
- Code: Model threats during design to guide secure coding practices.
- Build: Validate threat models during code reviews.
- Test: Use threat models to prioritize security testing.
- Deploy: Ensure mitigations are implemented in production.
- Monitor: Update threat models based on runtime telemetry.
Architecture & How It Works
Components and Internal Workflow
Threat modeling typically involves:
- System Decomposition: Break down the application into components (e.g., services, APIs).
- Threat Identification: Use frameworks like STRIDE or PASTA to identify threats.
- Risk Assessment: Evaluate threats based on likelihood and impact.
- Mitigation Planning: Define countermeasures (e.g., encryption, access controls).
- Validation: Review and update the model iteratively.
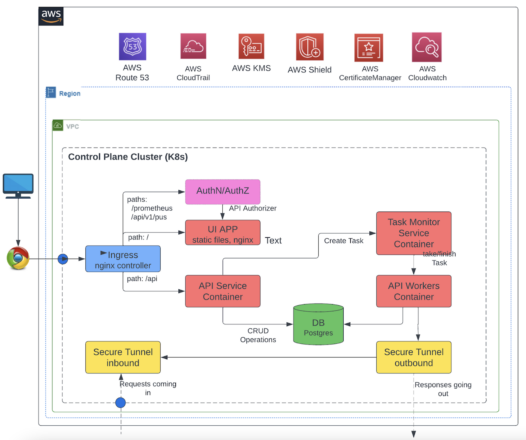
Architecture Diagram
The architecture diagram for threat modeling in DevSecOps includes:
- Inputs: System architecture, DFDs, and security requirements.
- Tools: Threat modeling tools like OWASP Threat Dragon or Microsoft Threat Modeling Tool.
- Process: A cyclical workflow of decomposition, threat identification, risk assessment, and mitigation.
- Outputs: Threat model document, mitigation plan, and integration with CI/CD pipelines.
Imagine a flowchart where the system architecture feeds into a DFD, which is processed by a threat modeling tool, producing a threat model that integrates with CI/CD tools like Jenkins or GitLab.
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: Embed threat modeling in pipelines using tools like Jenkins or GitHub Actions to automate DFD generation or threat analysis.
- Cloud Tools: Use cloud-native security tools (e.g., AWS Security Hub, Azure Defender) to validate threat models against cloud configurations.
- IaC Scanning: Integrate with tools like Terraform or Checkov to scan Infrastructure-as-Code for misconfigurations.
Installation & Getting Started
Basic Setup or Prerequisites
To start threat modeling, you need:
- A threat modeling tool (e.g., OWASP Threat Dragon, Microsoft Threat Modeling Tool).
- A system architecture diagram or DFD.
- Basic understanding of the application and its components.
- Access to a CI/CD environment (optional for automation).
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide uses OWASP Threat Dragon, an open-source threat modeling tool.
- Install Threat Dragon:
- Download from https://github.com/OWASP/Threat-Dragon or use the web version.
- For local installation, ensure Node.js is installed, then run:
npm install -g @owasp/threat-dragon threat-dragon
- Create a New Project:
- Open Threat Dragon and start a new project.
- Name the project (e.g., “E-commerce App Threat Model”).
- Draw a Data Flow Diagram:
- Add components (e.g., User, Web Server, Database).
- Connect them with data flows (e.g., HTTP requests, SQL queries).
- Identify Threats:
- Use the STRIDE framework to generate threats for each component.
- Example: For a database, identify “Information Disclosure” (e.g., SQL injection).
- Define Mitigations:
- For each threat, add mitigations (e.g., “Use prepared statements for SQL queries”).
- Export and Integrate:
- Export the threat model as JSON or PDF.
- Store in a version control system (e.g., Git) for CI/CD integration.
Real-World Use Cases
Threat modeling is applied across industries in DevSecOps. Here are four scenarios:
- E-commerce Platform:
- Scenario: Protect customer data during checkout.
- Threat Model: Identify threats like session hijacking or XSS.
- Mitigation: Implement secure session management, input validation.
- Healthcare Application:
- Scenario: Secure patient data in a telemedicine app.
- Threat Model: Focus on data leakage and unauthorized access.
- Mitigation: Use end-to-end encryption, HIPAA-compliant access controls.
- Financial Services API:
- Scenario: Secure a payment processing API.
- Threat Model: Address spoofing and tampering risks.
- Mitigation: Implement API key authentication, request signing.
- IoT Device Management:
- Scenario: Secure communication between IoT devices and cloud.
- Threat Model: Identify denial-of-service or firmware tampering.
- Mitigation: Use MQTT with TLS, regular firmware updates.
Benefits & Limitations
Key Advantages
- Proactive Security: Identifies vulnerabilities before exploitation.
- Team Collaboration: Bridges gaps between developers, security, and operations.
- Cost Savings: Reduces remediation costs by addressing issues early.
- Compliance: Aligns with regulatory requirements (e.g., GDPR, PCI-DSS).
Common Challenges or Limitations
- Complexity: Requires understanding of system architecture.
- Time-Intensive: Initial modeling can be resource-heavy.
- Tool Limitations: Some tools lack automation or cloud integration.
- False Positives: Over-identification of low-risk threats.
Best Practices & Recommendations
- Start Early: Perform threat modeling during the design phase.
- Automate Where Possible: Use scripts to generate DFDs or integrate with CI/CD:
# Example: Automate DFD generation with Python
import graphviz
dot = graphviz.Digraph()
dot.node('A', 'User')
dot.node('B', 'Web Server')
dot.edge('A', 'B', label='HTTP')
dot.render('dfd', format='png')- Regular Updates: Revisit threat models after major system changes.
- Compliance Alignment: Map mitigations to standards like NIST 800-53.
- Training: Educate teams on STRIDE or PASTA methodologies.
Comparison with Alternatives
| Criteria | STRIDE | PASTA | OWASP Threat Dragon |
|---|---|---|---|
| Ease of Use | Moderate | Complex | Beginner-Friendly |
| Automation | Limited | High | Moderate |
| Cloud Integration | Basic | Strong | Moderate |
| Best For | General Use | Enterprise | Open-Source Projects |
- When to Choose STRIDE: For quick, lightweight threat modeling.
- When to Choose PASTA: For complex, enterprise-grade systems with compliance needs.
- When to Choose Threat Dragon: For open-source or budget-constrained teams.
Conclusion
Threat modeling is a cornerstone of DevSecOps, enabling teams to build secure systems proactively. By integrating with CI/CD pipelines and cloud tools, it ensures security is continuous and collaborative. Future trends include increased automation, AI-driven threat analysis, and tighter integration with cloud-native architectures.
Next Steps:
- Start with OWASP Threat Dragon for hands-on practice.
- Explore advanced frameworks like PASTA for enterprise use.
- Join communities like OWASP or DevSecOps forums.