Introduction & Overview
In the rapidly evolving landscape of software development, ensuring security and compliance is paramount. A Software Bill of Materials (SBOM) has emerged as a critical tool in DevSecOps, enabling organizations to manage software components, track vulnerabilities, and ensure regulatory compliance. This tutorial provides a detailed exploration of SBOM, its integration into DevSecOps workflows, and practical guidance for implementation.
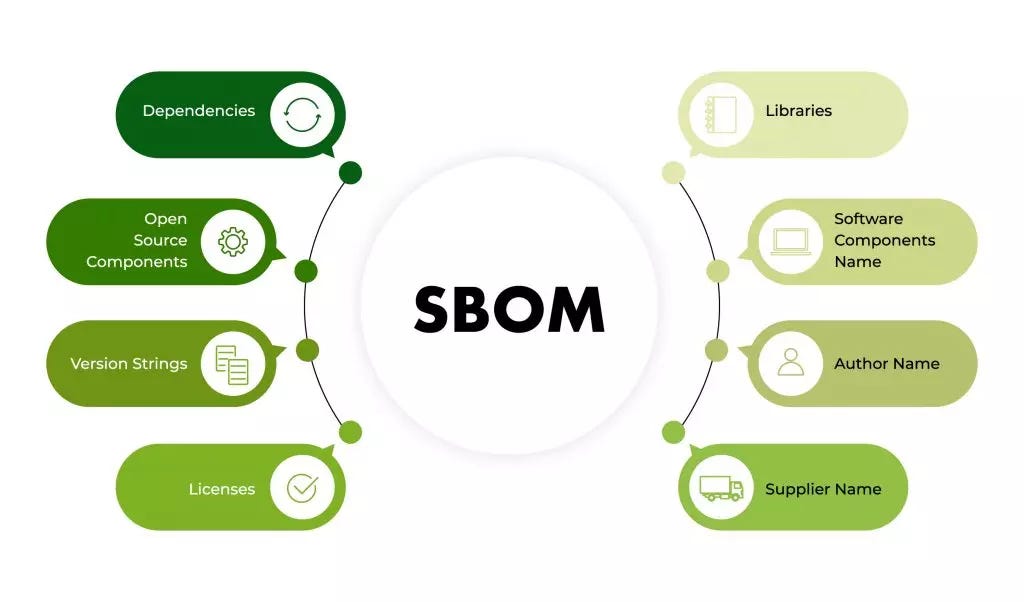
What is an SBOM (Software Bill of Materials)?
An SBOM is a structured, machine-readable inventory of all software components, libraries, and dependencies used in a software application or system. It includes metadata such as component names, versions, licenses, and origins, providing a transparent view of the software supply chain.
- Purpose: Enhances visibility into software composition to identify vulnerabilities, ensure compliance, and streamline dependency management.
- Formats: Common formats include SPDX (Software Package Data Exchange) and CycloneDX, available in JSON or XML.
- Analogy: Think of an SBOM as a “nutrition label” for software, listing all “ingredients” and their sources.
History or Background
The concept of an SBOM originated in the early 2000s as software supply chain complexity grew. Key milestones include:
- 2010s: The rise of open-source software and dependency-related vulnerabilities (e.g., Heartbleed in 2014) highlighted the need for better component tracking.
- 2018: The NTIA (National Telecommunications and Information Administration) initiated efforts to standardize SBOMs, promoting adoption in industries like healthcare and finance.
- 2021: The U.S. Executive Order on Improving the Nation’s Cybersecurity (EO 14028) mandated SBOMs for federal software, accelerating mainstream adoption.
- Present (2025): SBOMs are integral to DevSecOps, driven by regulatory requirements and increasing cyber threats.
Why is it Relevant in DevSecOps?
DevSecOps integrates security into every phase of the software development lifecycle (SDLC). SBOMs are critical because they:
- Enhance Security: Identify and mitigate vulnerabilities in dependencies early in the SDLC.
- Ensure Compliance: Align with regulations like GDPR, HIPAA, and EO 14028 by documenting software components and licenses.
- Improve Collaboration: Provide a shared artifact for development, security, and operations teams to align on risk management.
- Support Automation: Enable automated scanning and monitoring in CI/CD pipelines, reducing manual overhead.
Core Concepts & Terminology
Key Terms and Definitions
- Component: Any software element (e.g., library, framework, module) included in an application.
- Dependency: A component that the application relies on to function, often third-party or open-source.
- SPDX: An open standard for SBOMs, developed by the Linux Foundation, supporting license and vulnerability tracking.
- CycloneDX: An SBOM standard by OWASP, optimized for security and dependency graphing.
- Vulnerability: A weakness in a component that could be exploited, often tracked via CVE (Common Vulnerabilities and Exposures) identifiers.
- Provenance: The origin and history of a component, including its source and version.
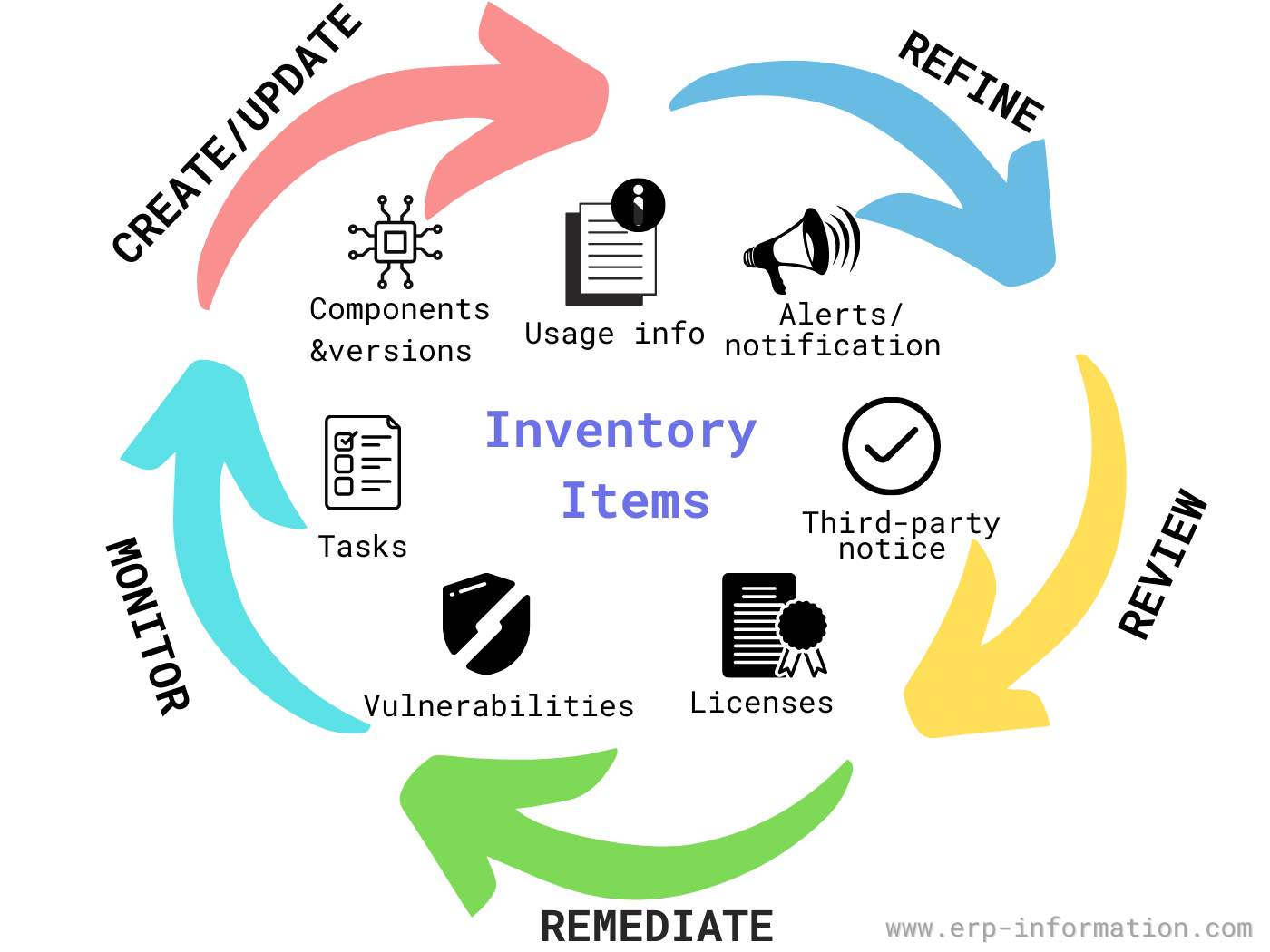
How SBOM Fits into the DevSecOps Lifecycle
SBOMs integrate into DevSecOps across the SDLC:
- Plan: Define SBOM generation as part of security requirements.
- Code: Generate SBOMs during development to track dependencies.
- Build: Integrate SBOM generation into CI/CD pipelines for real-time visibility.
- Test: Use SBOMs to scan for vulnerabilities using tools like Dependabot or Snyk.
- Release/Deploy: Share SBOMs with stakeholders to ensure compliance and transparency.
- Monitor: Continuously update SBOMs to reflect changes and monitor for new vulnerabilities.

graph TD
A[Code Commit] --> B[SBOM Generation]
B --> C[Security Scanning]
C --> D[Policy Enforcement]
D --> E[Deployment]
E --> F[Monitoring & Incident Response]
Architecture & How It Works
Components and Internal Workflow
An SBOM ecosystem typically includes:
- SBOM Generator: Tools like Syft, Trivy, or Dependency-Track that analyze codebases to produce SBOMs.
- Dependency Scanner: Identifies components and their versions (e.g., via
pom.xml,package.json). - Metadata Repository: Stores component details, including licenses and CVEs.
- Integration Layer: Connects SBOM tools with CI/CD pipelines, vulnerability databases (e.g., NVD), and compliance platforms.
- Consumer Tools: Security scanners, compliance checkers, or DevSecOps dashboards that use SBOM data.
Workflow:
- Discovery: The SBOM generator scans the codebase, container images, or runtime environment to identify components.
- Metadata Collection: Details like version, license, and origin are gathered.
- SBOM Generation: Data is formatted into SPDX or CycloneDX.
- Analysis: Tools cross-reference SBOMs with vulnerability databases.
- Reporting: SBOMs are shared with teams or regulators, often via APIs or dashboards.
Architecture Diagram Description
The diagram depicts a layered architecture:
- Top Layer (CI/CD Pipeline): GitHub Actions or Jenkins triggers SBOM generation during build.
- Middle Layer (SBOM Tools): Syft or Trivy generates SBOMs, feeding data to Dependency-Track.
- Data Layer: SBOMs are stored in a database (e.g., PostgreSQL) and linked to vulnerability feeds (e.g., NVD).
- Integration Points: APIs connect to DevSecOps tools (e.g., Snyk, Jira) and cloud platforms (e.g., AWS, Azure).
- Output: SBOMs are exported as JSON/XML files or visualized in dashboards.
Flow: Code commit → CI/CD triggers SBOM generation → SBOM stored → Vulnerability scan → Alerts to DevSecOps teams.
[ Source Code ] → [ Build System ] → [ SBOM Generator ]
↓
[ SBOM File (JSON/XML) ]
↓
[ Vulnerability Scanner | Policy Engine ]
Integration Points with CI/CD or Cloud Tools
- CI/CD: Integrate SBOM generation in pipelines using plugins (e.g., GitHub Actions for Syft).
- Cloud: AWS CodePipeline or Azure DevOps can ingest SBOMs for compliance checks.
- Security Tools: Snyk, Dependabot, or OWASP Dependency-Check use SBOMs for vulnerability scanning.
- Compliance Platforms: Tools like Black Duck or Sonatype map SBOMs to regulatory requirements.
Installation & Getting Started
Basic Setup or Prerequisites
To generate and use SBOMs in a DevSecOps environment, you’ll need:
- Operating System: Linux, macOS, or Windows.
- Tools: Docker (for container scanning), Git, and an SBOM generator (e.g., Syft or Trivy).
- CI/CD Platform: GitHub Actions, Jenkins, or GitLab CI.
- Dependencies: Python, Node.js, or Java (depending on the project).
- Access: API keys for vulnerability databases (e.g., NVD) or commercial tools (e.g., Snyk).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
Let’s set up Syft to generate an SBOM for a Node.js project and integrate it into a GitHub Actions pipeline.
- Install Syft:
curl -sSfL https://raw.githubusercontent.com/anchore/syft/main/install.sh | sh -s -- -b /usr/local/bin2. Create a Sample Node.js Project:
mkdir my-node-app && cd my-node-app
npm init -y
npm install express 3. Generate an SBOM:
Run Syft to create a CycloneDX JSON SBOM:
syft dir:. -o cyclonedx-json > sbom.json4. View the SBOM:
cat sbom.jsonExample output:
{
"bomFormat": "CycloneDX",
"specVersion": "1.4",
"components": [
{
"type": "library",
"name": "express",
"version": "4.18.2",
"purl": "pkg:npm/express@4.18.2"
}
]
}5. Integrate with GitHub Actions:
Create a .github/workflows/sbom.yml file:
name: Generate SBOM
on: [push]
jobs:
generate-sbom:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Install Syft
run: |
curl -sSfL https://raw.githubusercontent.com/anchore/syft/main/install.sh | sh -s -- -b /usr/local/bin
- name: Generate SBOM
run: syft dir:. -o cyclonedx-json > sbom.json
- name: Upload SBOM
uses: actions/upload-artifact@v3
with:
name: sbom
path: sbom.json6. Verify Vulnerabilities:
Use a tool like Grype to scan the SBOM:
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/bin
grype sbom:./sbom.json7. Automate in CI/CD: Push the code to GitHub, and the workflow will generate and store the SBOM.
Real-World Use Cases
Scenario 1: Vulnerability Management in a Web Application
A fintech company uses a Node.js application with multiple dependencies. By generating an SBOM with Syft and scanning it with Grype, the team identifies a critical CVE in an outdated Express version. They update the dependency and re-run the pipeline, ensuring no vulnerabilities before deployment.
Scenario 2: Compliance in Healthcare
A healthcare provider must comply with HIPAA, requiring transparency in software components. They use CycloneDX SBOMs to document all dependencies in a medical records system, sharing them with auditors to prove compliance with licensing and security standards.
Scenario 3: Container Security in Cloud Deployments
A DevOps team deploys Docker containers to AWS. They use Trivy to generate SBOMs for container images, integrating them into AWS CodePipeline. This ensures all container dependencies are scanned for vulnerabilities before deployment.
Scenario 4: Open-Source License Management
An e-commerce company uses Dependency-Track to manage SBOMs for their Python-based platform. They identify non-compliant licenses (e.g., GPL) in dependencies, replacing them to avoid legal risks.
Industry-Specific Example
In automotive, SBOMs are used to secure software in connected vehicles, aligningWITH standards like ISO/SAE 21434. Manufacturers generate SBOMs for embedded systems to track vulnerabilities and ensure compliance with cybersecurity regulations.
Benefits & Limitations
Key Advantages
- Transparency: Provides a clear view of software components, aiding audits and troubleshooting.
- Security: Enables proactive vulnerability detection and remediation.
- Compliance: Aligns with regulations like EO 14028, GDPR, and HIPAA.
- Automation: Integrates seamlessly with CI/CD for real-time monitoring.
Common Challenges or Limitations
- Complexity: Generating and maintaining SBOMs for large codebases can be resource-intensive.
- Accuracy: Incomplete or outdated SBOMs may miss critical dependencies.
- Tooling Gaps: Not all tools support both SPDX and CycloneDX or integrate with all CI/CD systems.
- Adoption: Requires cultural shift in teams to prioritize SBOM usage.
Best Practices & Recommendations
Security Tips
- Automate SBOM Generation: Use tools like Syft or Trivy in CI/CD pipelines to ensure consistency.
- Regular Updates: Re-generate SBOMs after every code or dependency change.
- Vulnerability Scanning: Pair SBOMs with tools like Grype or Snyk for continuous monitoring.
Performance
- Optimize Scans: Limit SBOM generation to relevant directories to reduce processing time.
- Cache Dependencies: Store SBOMs in a repository to avoid redundant scans.
Maintenance
- Version Control: Store SBOMs in Git alongside code for traceability.
- Periodic Reviews: Audit SBOMs quarterly to ensure accuracy and compliance.
Compliance Alignment
- Map SBOM metadata to regulatory requirements (e.g., license types for GDPR).
- Use tools like Dependency-Track to generate compliance reports.
Automation Ideas
- Integrate SBOM generation with GitHub Actions or Jenkins for real-time updates.
- Use APIs to push SBOMs to security dashboards or compliance platforms.
Comparison with Alternatives
| Feature | SBOM (SPDX/CycloneDX) | Dependency Scanning (e.g., Snyk) | Manual Audits |
|---|---|---|---|
| Purpose | Comprehensive component inventory | Vulnerability detection in dependencies | Ad-hoc component tracking |
| Automation | High (CI/CD integration) | High (real-time scanning) | Low (manual effort) |
| Compliance Support | Strong (standardized formats) | Moderate (limited metadata) | Weak (inconsistent) |
| Scalability | High (machine-readable) | High (cloud-based) | Low (human-dependent) |
| Cost | Low (open-source tools) | Medium to High (subscription-based) | High (labor-intensive) |
| Use Case | Full supply chain visibility | Targeted vulnerability fixes | Small-scale audits |
When to Choose SBOM
- Choose SBOM: For compliance, transparency, and broad supply chain visibility.
- Choose Alternatives: Use dependency scanners for quick vulnerability fixes or manual audits for small, non-automated projects.
Conclusion
SBOMs are a cornerstone of modern DevSecOps, providing transparency, security, and compliance in software development. By integrating SBOMs into CI/CD pipelines, teams can proactively manage vulnerabilities and align with regulatory standards. As cyber threats and regulations evolve, SBOM adoption will likely grow, with emerging trends like AI-driven SBOM analysis and blockchain-based provenance tracking.
Next Steps:
- Start with open-source tools like Syft or Trivy for SBOM generation.
- Integrate SBOMs into your CI/CD pipeline for automation.
- Explore advanced tools like Dependency-Track for enterprise-scale management.