Introduction & Overview
Web Application Firewalls (WAFs) are critical components in modern cybersecurity, protecting web applications from threats like SQL injection, cross-site scripting (XSS), and other OWASP Top Ten vulnerabilities. In the context of DevSecOps, WAFs bridge development, security, and operations by embedding security controls into the software development lifecycle (SDLC). This tutorial provides a detailed exploration of WAFs, covering their concepts, architecture, setup, use cases, benefits, limitations, and best practices, tailored for DevSecOps practitioners.
What is a Web Application Firewall (WAF)?
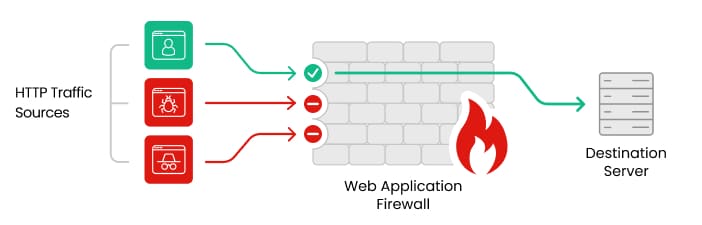
A WAF is a security solution that monitors, filters, and blocks HTTP/HTTPS traffic to and from web applications based on predefined rules. Positioned between the client and the web server, it inspects requests and responses to detect and mitigate malicious activities.
- Purpose: Protects against application-layer attacks (Layer 7 in the OSI model).
- Deployment: Can be cloud-based, on-premises, or integrated into a reverse proxy.
- Key Features: Rule-based filtering, anomaly detection, and virtual patching.
History or Background
WAFs emerged in the late 1990s as web applications became prime targets for cyberattacks. Early solutions focused on basic request filtering, evolving into sophisticated systems with machine learning and behavioral analysis by the 2010s. The rise of DevSecOps in the 2010s emphasized integrating WAFs into CI/CD pipelines, aligning security with agile development.
Why is it Relevant in DevSecOps?
DevSecOps integrates security into every phase of the SDLC, and WAFs play a pivotal role by:
- Automating Security: Enforcing security policies in CI/CD pipelines.
- Shift-Left Security: Enabling early detection of vulnerabilities during development.
- Continuous Monitoring: Providing real-time protection in production.
- Compliance: Aligning with standards like PCI-DSS, HIPAA, and GDPR.
Core Concepts & Terminology
Understanding WAFs requires familiarity with essential terms and their integration into DevSecOps workflows.
Key Terms and Definitions
- Rule Set: Predefined or custom policies to identify malicious patterns (e.g., ModSecurity OWASP Core Rule Set).
- Positive Security Model: Allows only known good traffic (whitelisting).
- Negative Security Model: Blocks known bad traffic (blacklisting).
- Virtual Patching: Temporarily mitigates vulnerabilities without changing application code.
- Anomaly Detection: Identifies deviations from normal traffic patterns using machine learning or heuristics.
| Term | Definition |
|---|---|
| WAF | Filters HTTP/S requests to protect against attacks targeting web apps |
| Blacklist | Deny traffic that matches known attack patterns |
| Whitelist | Allow only known safe traffic |
| Positive Security Model | Allows only well-defined inputs (whitelisting) |
| Negative Security Model | Blocks known bad patterns (blacklisting) |
| Virtual Patching | Blocking exploits before fixing the codebase |
| Rule Set | Predefined filters for identifying common threats (e.g., OWASP CRS) |
How it Fits into the DevSecOps Lifecycle
WAFs align with DevSecOps by:
- Plan: Defining security policies in IaC (Infrastructure as Code) templates.
- Code: Integrating WAF rules with application development.
- Build/Test: Validating WAF configurations in CI/CD pipelines.
- Deploy/Operate: Enforcing runtime protection and monitoring.
- Monitor: Analyzing logs for incident response and compliance.
Architecture & How It Works
WAFs operate as a protective layer, analyzing HTTP traffic and applying security rules.
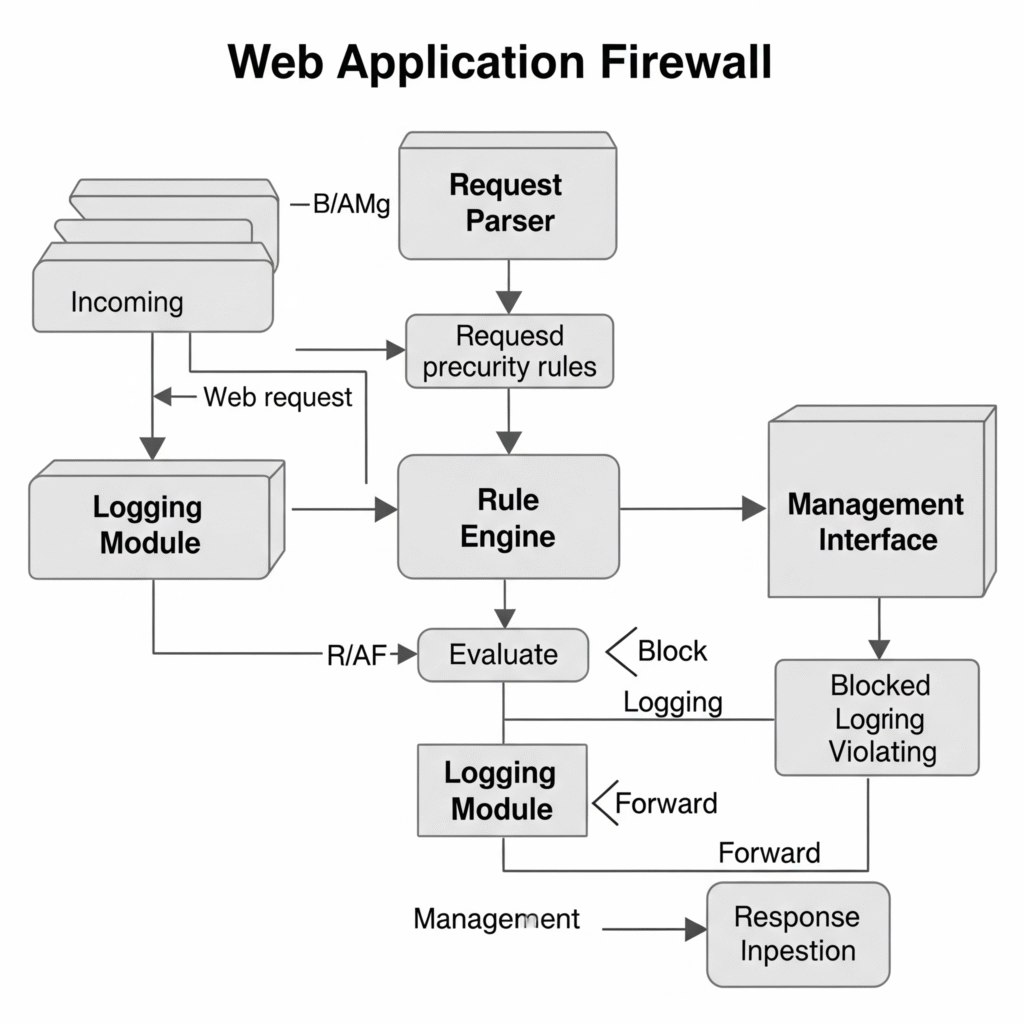
Components and Internal Workflow
- Request Parser: Decodes HTTP/HTTPS requests (headers, payloads, cookies).
- Rule Engine: Matches traffic against rule sets to allow, block, or log.
- Logging Module: Records events for auditing and analysis.
- Management Interface: Configures rules, policies, and integrations.
Workflow:
- Client sends an HTTP request to the web application.
- WAF intercepts and parses the request.
- Rule engine evaluates the request against policies.
- If malicious, the request is blocked or logged; otherwise, it’s forwarded to the server.
- Server response is inspected before reaching the client.
Architecture Diagram (Description)
Imagine a layered architecture:
- Client Layer: End-users or bots sending HTTP requests.
- WAF Layer: A reverse proxy or cloud service (e.g., AWS WAF, Cloudflare) inspecting traffic.
- Application Layer: Web servers (e.g., Nginx, Apache) hosting the application.
- Backend Layer: Databases or APIs processing requests.
[User]
|
v
[CDN/Load Balancer]
|
v
[WAF Engine] --> [WAF Ruleset DB]
|
v
[Application Servers]
Arrows depict bidirectional traffic flow through the WAF, with a logging module capturing events for analysis.
Integration Points with CI/CD or Cloud Tools
- CI/CD: WAF rules in IaC (e.g., Terraform for AWS WAF):
resource "aws_wafv2_web_acl" "example" {
name = "example-acl"
scope = "REGIONAL"
default_action {
allow {}
}
rule {
name = "block-sql-injection"
priority = 1
statement {
managed_rule_group_statement {
name = "AWSManagedRulesSQLiRuleSet"
vendor_name = "AWS"
}
}
action {
block {}
}
}
}- Cloud Tools: Integrates with AWS ALB, Azure Application Gateway, or Cloudflare for scalable deployment.
- Monitoring: Feeds logs to SIEM tools (e.g., Splunk, ELK Stack) for real-time analysis.
Installation & Getting Started
This section outlines the prerequisites and a step-by-step guide to set up ModSecurity, an open-source WAF, with Nginx.
Basic Setup or Prerequisites
- OS: Ubuntu 20.04 or later.
- Software: Nginx, ModSecurity, OWASP Core Rule Set (CRS).
- Hardware: Minimum 2GB RAM, 2-core CPU.
- Permissions: Root or sudo access.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
- Install Nginx and Dependencies:
sudo apt update
sudo apt install -y nginx libmodsecurity3 modsecurity-crs- Configure ModSecurity:
sudo cp /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
sudo nano /etc/modsecurity/modsecurity.confEnable detection by changing SecRuleEngine DetectionOnly to SecRuleEngine On.
- Include OWASP CRS:
sudo nano /etc/nginx/nginx.confAdd to the http block:
include /usr/share/modsecurity-crs/*.conf;- Test Configuration:
sudo nginx -t
sudo systemctl restart nginx- Verify WAF:
Test with a malicious URL (e.g.,http://your-server/?id=1%20OR%201=1) and check logs:
sudo tail -f /var/log/modsecurity/audit.logReal-World Use Cases
WAFs are applied across industries to enhance security in DevSecOps workflows.
- E-commerce (PCI-DSS Compliance): Protects payment gateways from XSS and SQL injection. Example: AWS WAF blocks malicious requests to a Shopify store’s checkout page.
- Healthcare (HIPAA Compliance): Secures patient portals by filtering sensitive data leaks. Example: Azure WAF prevents unauthorized access to a hospital’s appointment system.
- Finance (Fraud Prevention): Detects and blocks brute-force login attempts. Example: Cloudflare WAF mitigates credential stuffing on a banking app.
- API Security: Protects REST APIs in microservices. Example: A WAF filters malformed JSON payloads in a CI/CD-deployed API gateway.
Benefits & Limitations
Key Advantages
- Proactive Protection: Mitigates OWASP Top Ten threats in real-time.
- Scalability: Cloud-based WAFs (e.g., AWS WAF) scale with traffic.
- Compliance: Simplifies adherence to PCI-DSS, GDPR, and HIPAA.
- Virtual Patching: Reduces downtime by addressing vulnerabilities without code changes.
Common Challenges or Limitations
- False Positives: Legitimate traffic may be blocked due to strict rules.
- Performance Overhead: On-premises WAFs can introduce latency.
- Complex Configuration: Requires expertise to tune rules effectively.
- Limited Layer 7 Scope: Ineffective against network-layer attacks (e.g., DDoS).
Best Practices & Recommendations
- Security Tips:
- Use managed rule sets (e.g., OWASP CRS) for baseline protection.
- Regularly update rules to address new vulnerabilities.
- Performance:
- Optimize rule sets to minimize latency.
- Use cloud-based WAFs for auto-scaling.
- Maintenance:
- Monitor logs for false positives and adjust rules.
- Automate rule updates via CI/CD pipelines.
- Compliance Alignment: Map WAF rules to specific compliance requirements (e.g., PCI-DSS 6.6).
- Automation Ideas: Use Terraform or Ansible to deploy and update WAF configurations.
Comparison with Alternatives
| Feature | WAF | IDS/IPS | API Gateway |
|---|---|---|---|
| Layer Focus | Application (L7) | Network (L3-L4) | Application (L7) |
| Threat Protection | XSS, SQLi | DDoS, Malware | API-specific |
| CI/CD Integration | High | Medium | High |
| Scalability | Cloud/On-prem | On-prem | Cloud |
| Ease of Setup | Moderate | Complex | Moderate |
When to Choose a WAF
- WAF: Best for protecting web applications from Layer 7 attacks, especially in DevSecOps with CI/CD integration.
- IDS/IPS: Suited for network-level threat detection.
- API Gateway: Ideal for API-specific security and rate limiting.
Conclusion
WAFs are indispensable in DevSecOps, providing robust protection for web applications while aligning with agile and secure development practices. As threats evolve, WAFs are incorporating AI-driven anomaly detection and deeper cloud integrations. Future trends include serverless WAFs and enhanced automation in CI/CD pipelines.