Introduction & Overview
What are Admission Controllers?
Admission Controllers are Kubernetes plugins that intercept and process requests to the Kubernetes API server before objects (e.g., pods, deployments) are persisted. They enforce policies, validate configurations, or mutate resources to ensure compliance with organizational standards.
History or Background
Introduced in Kubernetes 1.0 (2015), Admission Controllers have evolved to address growing needs for security and governance in containerized environments. Initially focused on basic validation, they now support dynamic policy enforcement through webhooks, aligning with DevSecOps principles of integrating security into the development lifecycle.
Why is it Relevant in DevSecOps?
In DevSecOps, security is embedded into every phase of the software delivery pipeline. Admission Controllers play a pivotal role by:
- Enforcing security policies (e.g., restricting untrusted images).
- Automating compliance checks (e.g., ensuring resource limits).
- Enabling rapid feedback loops for developers.
- Reducing manual security reviews by codifying policies.
Core Concepts & Terminology
Key Terms and Definitions
- Validating Admission Controller: Rejects or allows API requests based on predefined rules (e.g., PodSecurityStandards).
- Mutating Admission Controller: Modifies API requests before persistence (e.g., injecting sidecar containers).
- Webhook: External service called by the Kubernetes API to process admission requests.
- Namespace: Logical isolation within a Kubernetes cluster where policies can be applied.
- Policy: A rule or set of rules enforced by an Admission Controller.
| Term | Definition |
|---|---|
| Mutating Webhook | Modifies requests before persistence (e.g., injecting sidecars) |
| Validating Webhook | Accepts or rejects requests based on custom logic |
| Admission Webhook | External HTTP callback used to validate/mutate API requests |
| API Server | Core Kubernetes component that handles REST requests to the cluster |
| OPA/Gatekeeper | Policy engine for Kubernetes Admission Control, based on Open Policy Agent |
| Kyverno | Kubernetes-native policy engine focused on Admission Control |
How It Fits into the DevSecOps Lifecycle
Admission Controllers integrate into the DevSecOps lifecycle by:
- Shift-Left Security: Validating configurations during development or CI/CD.
- Automation: Enforcing policies without manual intervention.
- Continuous Compliance: Ensuring deployments meet regulatory standards (e.g., PCI-DSS, HIPAA).
- Feedback Loop: Providing immediate feedback to developers on policy violations.
[Code Commit] --> [CI Build] --> [Admission Controller (Validation)] --> [Deploy to Cluster]
|
[Reject or mutate invalid manifests]
Architecture & How It Works
Components and Internal Workflow
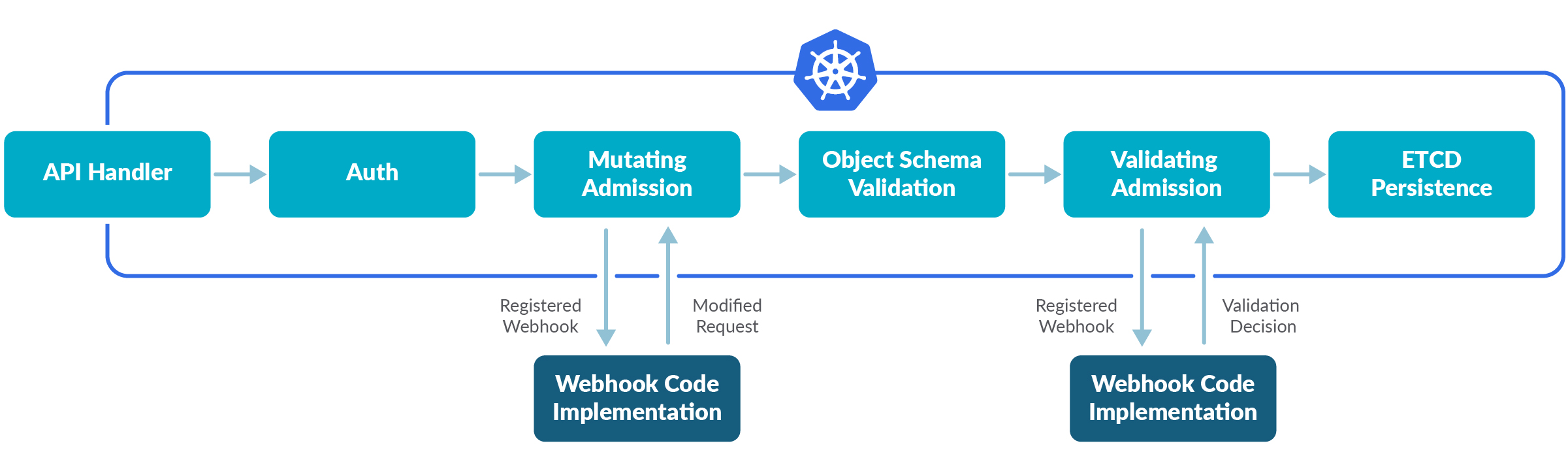
Admission Controllers operate within the Kubernetes API server’s request processing pipeline:
- Authentication and Authorization: The API server verifies the user’s identity and permissions.
- Mutation Phase: Mutating controllers modify the resource (e.g., adding labels).
- Validation Phase: Validating controllers check the resource against policies.
- Persistence: If approved, the resource is saved to etcd.
Architecture Diagram
The architecture can be visualized as a flowchart. An API request enters the Kubernetes API server, passing through authentication and authorization modules. It then reaches the Admission Controller chain, split into mutating and validating phases. Mutating controllers (e.g., sidecar injectors) modify the request, followed by validating controllers (e.g., OPA Gatekeeper) that enforce policies. If all checks pass, the request is persisted to etcd. External webhooks may be called during either phase to extend functionality.
[User/CI]
↓
[API Server]
↓
[Mutating Webhook] (e.g., inject sidecar)
↓
[Validating Webhook] (e.g., enforce security policies)
↓
[etcd / Cluster State]
Integration Points with CI/CD or Cloud Tools
Admission Controllers integrate with:
- CI/CD Pipelines: Tools like Jenkins or GitLab CI/CD trigger deployments that Admission Controllers validate.
- Policy Engines: Open Policy Agent (OPA) or Kyverno for dynamic policy enforcement.
- Cloud Providers: AWS, Azure, or GCP Kubernetes services use Admission Controllers for cloud-specific policies.
- Observability Tools: Prometheus or Grafana to monitor policy violations.
Installation & Getting Started
Basic Setup or Prerequisites
- Kubernetes cluster (v1.16+ recommended).
- Admin access to the cluster.
- Familiarity with YAML and kubectl.
- Optional: Policy engine like OPA Gatekeeper or Kyverno.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide sets up OPA Gatekeeper as an Admission Controller to enforce a policy that restricts container images to a trusted registry.
- Install OPA Gatekeeper:
kubectl apply -f https://raw.githubusercontent.com/open-policy-agent/gatekeeper/release-3.9/deploy/gatekeeper.yaml- Verify Installation:
kubectl get pods -n gatekeeper-system- Create a Constraint Template:
Save the following astrusted-registry.yaml:
apiVersion: templates.gatekeeper.sh/v1
kind: ConstraintTemplate
metadata:
name: k8strustedregistry
spec:
crd:
spec:
names:
kind: K8sTrustedRegistry
targets:
- target: admission.k8s.gatekeeper.sh
rego:
code: |
package k8strustedregistry
violation[{"msg": msg}] {
container := input.review.object.spec.containers[_]
not startswith(container.image, "docker.io/")
msg := sprintf("Container image %v is not from trusted registry", [container.image])
}Apply it:
kubectl apply -f trusted-registry.yaml- Create a Constraint:
Save the following asconstraint.yaml:
apiVersion: constraints.gatekeeper.sh/v1
kind: K8sTrustedRegistry
metadata:
name: trusted-registry
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Pod"]Apply it:
kubectl apply -f constraint.yaml- Test the Policy:
Try deploying a pod with an untrusted image:
kubectl run nginx --image=nginx:latestThis should fail with an error indicating the image is not from docker.io.
Real-World Use Cases
- Enforcing Trusted Image Registries: A financial institution uses Admission Controllers to ensure all container images come from a private, vetted registry, aligning with PCI-DSS compliance.
- Resource Limit Enforcement: A SaaS provider uses a mutating Admission Controller to automatically inject CPU and memory limits into pods, preventing resource abuse.
- Namespace-Based Policies: A healthcare organization enforces HIPAA-compliant configurations by restricting sensitive workloads to specific namespaces.
- Sidecar Injection: An e-commerce platform uses a mutating Admission Controller to inject logging sidecars into every pod for centralized monitoring.
Benefits & Limitations
Key Advantages
- Automation: Reduces manual security checks.
- Scalability: Applies policies cluster-wide.
- Flexibility: Supports custom policies via webhooks.
- Compliance: Aligns with regulatory standards.
Common Challenges or Limitations
- Complexity: Writing and testing policies (e.g., Rego for OPA) can be complex.
- Performance: Multiple controllers may increase API latency.
- Debugging: Policy violations can be hard to troubleshoot without proper logging.
Best Practices & Recommendations
- Security Tips: Use least privilege for webhook services and encrypt communications.
- Performance: Limit the number of active Admission Controllers to reduce latency.
- Maintenance: Regularly update policy definitions and test in a staging environment.
- Compliance: Align policies with standards like NIST or ISO 27001.
- Automation: Integrate with CI/CD for policy-as-code workflows.
Comparison with Alternatives
| Feature | Admission Controllers | Kyverno | PodSecurityPolicy (Deprecated) |
|---|---|---|---|
| Policy Enforcement | Validating & Mutating | Validating & Mutating | Validating Only |
| Ease of Use | Moderate (Webhook setup) | High (YAML-based) | Low (Complex config) |
| Extensibility | High (Custom webhooks) | High (Custom policies) | Low (Fixed rules) |
| Maintenance | Moderate | Low | High (Deprecated) |
| When to Choose | Custom policies, webhooks | Simple YAML policies | Legacy clusters |
Use Admission Controllers for flexible, webhook-based policy enforcement. Choose Kyverno for simpler, YAML-based policies, especially in smaller clusters.
Conclusion
Admission Controllers are a cornerstone of DevSecOps in Kubernetes, enabling automated security and compliance at scale. As Kubernetes adoption grows, their role in enforcing policies will expand, with trends like AI-driven policy optimization on the horizon. To get started, explore the official Kubernetes documentation (https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/) and join communities like the Kubernetes Slack or CNCF forums.