
1. Introduction & Overview
What is AWS IAM?
AWS Identity and Access Management (IAM) is a secure and flexible way to manage access to AWS services and resources. IAM enables you to:
- Control who can access your resources (authentication)
- Define what actions they can perform (authorization)
Background
- Launched in 2011 as part of AWS’s security and access control suite.
- Developed in response to growing enterprise need for fine-grained control over cloud resources.
- Has evolved to support federated identities, service roles, and permission boundaries.
Why IAM is Crucial in DevSecOps
In DevSecOps, security is embedded into every stage of the CI/CD pipeline. IAM plays a central role by:
- Automating least-privilege access across development, test, and production.
- Enforcing identity-based security policies within cloud-native pipelines.
- Supporting infrastructure as code (IaC) via permissions and policies.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Description |
|---|---|
| User | Represents a person or service that interacts with AWS resources. |
| Group | A collection of IAM users with shared permissions. |
| Role | Assignable identity with permissions used by trusted entities. |
| Policy | JSON document defining permissions (allow or deny). |
| Permission Boundary | Optional policy that sets maximum permissions a role/user can have. |
| Federation | Grants access using external identity providers like Okta or Active Directory. |
IAM in the DevSecOps Lifecycle
IAM fits across all stages:
- Plan: Define access control as code.
- Develop: Enforce identity-based access for dev environments.
- Build/Test: Limit CI/CD roles to scoped resources.
- Release: Use roles and policies for deployments.
- Operate: Audit access logs and rotate credentials.
- Monitor: Integrate IAM with AWS CloudTrail for real-time monitoring.
3. Architecture & How It Works
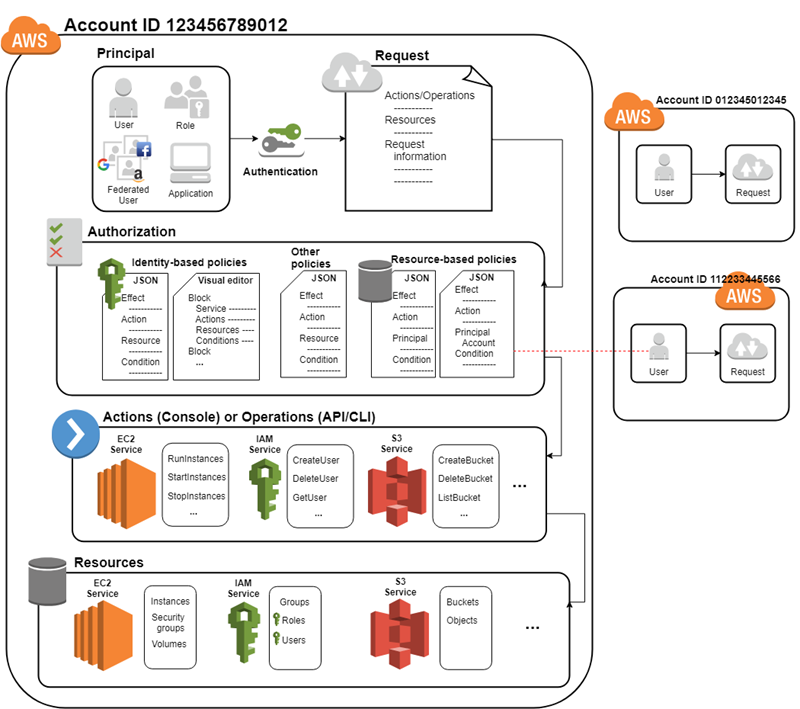
High-Level Workflow
- User/Role Authentication
- Policy Evaluation
- Authorization Decision
- Action Execution or Denial
IAM Architecture Diagram (Described)
- IAM Root
- Admin Access
- IAM Users
- Developers, testers, etc.
- Groups
- Grouped by roles (DevOps, QA)
- Roles
- Cross-account or federated access
- Policies
- Attached to users, groups, or roles
Trust Policy → Defines who can assume a role
Permissions Policy → Defines what actions the entity can take
Integration with CI/CD Tools
| Tool | IAM Integration |
|---|---|
| Jenkins | IAM roles for EC2 slaves and agents |
| GitHub Actions | OIDC-based authentication for temporary role assumption |
| GitLab CI | IAM credentials via environment variables or AssumeRole |
4. Installation & Getting Started
Prerequisites
- AWS account
- AWS CLI installed
- IAM administrative access
- Optional: Terraform or CloudFormation for IaC
Step-by-Step: Beginner IAM Setup
Step 1: Create a User
aws iam create-user --user-name devops-engineerStep 2: Attach Policy
aws iam attach-user-policy \
--user-name devops-engineer \
--policy-arn arn:aws:iam::aws:policy/AdministratorAccessStep 3: Create Access Keys (Use Securely!)
aws iam create-access-key --user-name devops-engineerStep 4: Create a Role for CI/CD
aws iam create-role \
--role-name CICDDeploymentRole \
--assume-role-policy-document file://trust-policy.jsontrust-policy.json:
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {"Service": "ec2.amazonaws.com"},
"Action": "sts:AssumeRole"
}]
}Step 5: Attach Policies to Role
aws iam attach-role-policy \
--role-name CICDDeploymentRole \
--policy-arn arn:aws:iam::aws:policy/AmazonS3FullAccess5. Real-World Use Cases
1. CI/CD Pipeline Access Control
- IAM roles allow GitHub Actions to deploy to AWS using OIDC-based AssumeRole.
- Eliminates long-term credentials in repositories.
2. Environment Segmentation
- Developers get IAM roles with permissions only to dev and staging resources.
- Prevents accidental access to production.
3. Secure Cloud Automation
- Terraform uses IAM users/roles with limited permissions to apply infrastructure changes.
- Prevents privilege escalation.
4. Serverless Function Execution
- AWS Lambda functions are assigned IAM roles with only the permissions they need.
- Supports least privilege in serverless deployments.
Industry Examples
- Finance: Role-based access for auditors using time-limited credentials.
- Healthcare: Fine-grained IAM policies ensure HIPAA compliance.
- Retail: Scoped permissions for third-party delivery systems via IAM roles.
6. Benefits & Limitations
Benefits
- Granular Access Control: Down to individual API actions.
- No Cost: IAM is free with AWS.
- Federation Support: Works with enterprise SSO.
- Scalable: Supports large orgs with thousands of users.
Limitations
- Complexity: Policies can become difficult to manage.
- Debugging: Determining why access was denied can be non-trivial.
- Hard Limits: 5000 roles per account (as of 2025; subject to change).
7. Best Practices & Recommendations
Security Tips
- Use Roles instead of long-term user credentials.
- Enable MFA for all IAM users.
- Rotate Keys regularly or use temporary credentials.
- Apply Least Privilege Principle rigorously.
Performance & Maintenance
- Audit access with CloudTrail.
- Use Access Analyzer to find overly permissive roles.
- Periodically review and prune unused IAM entities.
Compliance Alignment
- Tag IAM entities with compliance metadata.
- Use AWS Organizations SCPs to enforce global restrictions.
- Automate IAM setup using IaC (Terraform, AWS CDK).
8. Comparison with Alternatives
| Feature | AWS IAM | Azure AD | GCP IAM |
|---|---|---|---|
| Native AWS Access | ✅ | ❌ | ❌ |
| Fine-Grained Control | ✅ | ✅ | ✅ |
| Federation Support | ✅ | ✅ | ✅ |
| DevSecOps Integration | ✅ | Moderate | Moderate |
| Cost | Free | Paid tiers | Free |
When to Choose AWS IAM
- You’re running workloads entirely or primarily on AWS.
- Need tight CI/CD integration with AWS services.
- Require policy-as-code and automation capabilities.
9. Conclusion
AWS IAM is a cornerstone of secure DevSecOps practices in the AWS ecosystem. It empowers teams to enforce least privilege, integrate securely with pipelines, and build compliant cloud-native applications.
Future Trends
- Policy as code integration with tools like Open Policy Agent (OPA)
- Improved role federation with third-party identity providers
- AI-powered access analyzer tools for risk detection