Introduction & Overview
What is Kyverno?
Kyverno, derived from the Greek word for “govern,” is an open-source policy engine designed specifically for Kubernetes. It enables platform engineers and DevSecOps practitioners to define, enforce, and validate policies as Kubernetes-native resources using YAML. Unlike general-purpose policy engines, Kyverno leverages Kubernetes Custom Resource Definitions (CRDs) to manage policies without requiring users to learn a new language, making it highly accessible for Kubernetes administrators and developers. Kyverno supports validation, mutation, generation, and cleanup of Kubernetes resources, ensuring security, compliance, and operational efficiency in cloud-native environments.

History or Background
Kyverno was developed by Nirmata, a cloud-native platform company, and open-sourced under the Apache-2.0 license. It has gained significant traction, achieving Incubating status in the Cloud Native Computing Foundation (CNCF) with over 5,000 GitHub stars and 300+ contributors as of 2023. Initially built for Kubernetes, Kyverno has evolved to support broader use cases, including policy enforcement for JSON payloads like Terraform resources and software supply chain security through container image verification. Its focus on Kubernetes-native workflows and seamless integration with existing tools has made it a cornerstone for policy-as-code in cloud-native ecosystems.
Why is it Relevant in DevSecOps?
In DevSecOps, security is integrated into every phase of the software development lifecycle (SDLC), emphasizing automation, collaboration, and continuous security. Kyverno aligns with these principles by:
- Automating Security Policies: Enforces security best practices (e.g., blocking non-compliant resources) and compliance requirements in CI/CD pipelines.
- Shifting Security Left: Validates and mutates resources during the admission phase, catching issues early in the development process.
- Enabling Collaboration: Uses Kubernetes-native YAML, reducing the learning curve for development, security, and operations teams.
- Supporting Compliance: Generates policy reports and ensures adherence to standards like CIS benchmarks or NIST guidelines.
Kyverno’s ability to integrate with CI/CD pipelines and Kubernetes admission controllers makes it a critical tool for securing cloud-native applications, reducing vulnerabilities, and fostering a security-first culture.
Core Concepts & Terminology
Key Terms and Definitions
- Policy: A Kubernetes resource (ClusterPolicy or Policy) defining rules for validation, mutation, generation, or cleanup of resources.
- Validation: Checks if a resource complies with defined policies, either allowing or blocking it (e.g., ensuring Pods have specific labels).
- Mutation: Modifies resources dynamically to enforce best practices (e.g., adding resource limits to Pods).
- Generation: Creates new resources based on policy triggers (e.g., generating image pull secrets in new namespaces).
- Cleanup: Removes non-compliant or outdated resources.
- Admission Controller: A Kubernetes component that intercepts API requests to validate or mutate resources before they are persisted.
- Webhook: Kyverno’s mechanism to receive and process Kubernetes API server requests.
- Policy Report: A summary of policy violations or compliance status for cluster resources.
How It Fits into the DevSecOps Lifecycle
Kyverno integrates into the DevSecOps lifecycle across the following stages:
- Plan: Define policies for security and compliance (e.g., requiring specific labels or resource limits).
- Code: Validate code manifests in CI/CD pipelines using the Kyverno CLI.
- Build: Ensure container images meet security standards (e.g., verified signatures).
- Test: Use audit mode to identify non-compliant resources without blocking deployments.
- Deploy: Enforce policies in real-time via admission controllers to prevent misconfigurations.
- Monitor: Generate policy reports to track compliance and vulnerabilities continuously.
By embedding security checks early and automating enforcement, Kyverno reduces the risk of deploying insecure configurations and supports a “shift-left” security approach.
Architecture & How It Works
Components and Internal Workflow
Kyverno operates as a dynamic admission controller within a Kubernetes cluster, processing admission webhook requests from the Kubernetes API server. Its key components include:
- Webhook Server: Handles incoming AdmissionReview requests and forwards them to the policy engine.
- Policy Engine: Evaluates resources against defined policies, applying validation, mutation, or generation rules.
- Webhook Controller: Dynamically configures webhooks based on installed policies to optimize performance.
- Cert Renewer: Manages TLS certificates for secure webhook communication.
- Background Controller: Processes generate and mutate-existing policies via UpdateRequests.
- Report Controllers: Generate policy reports from Admission and Background Scan Reports.
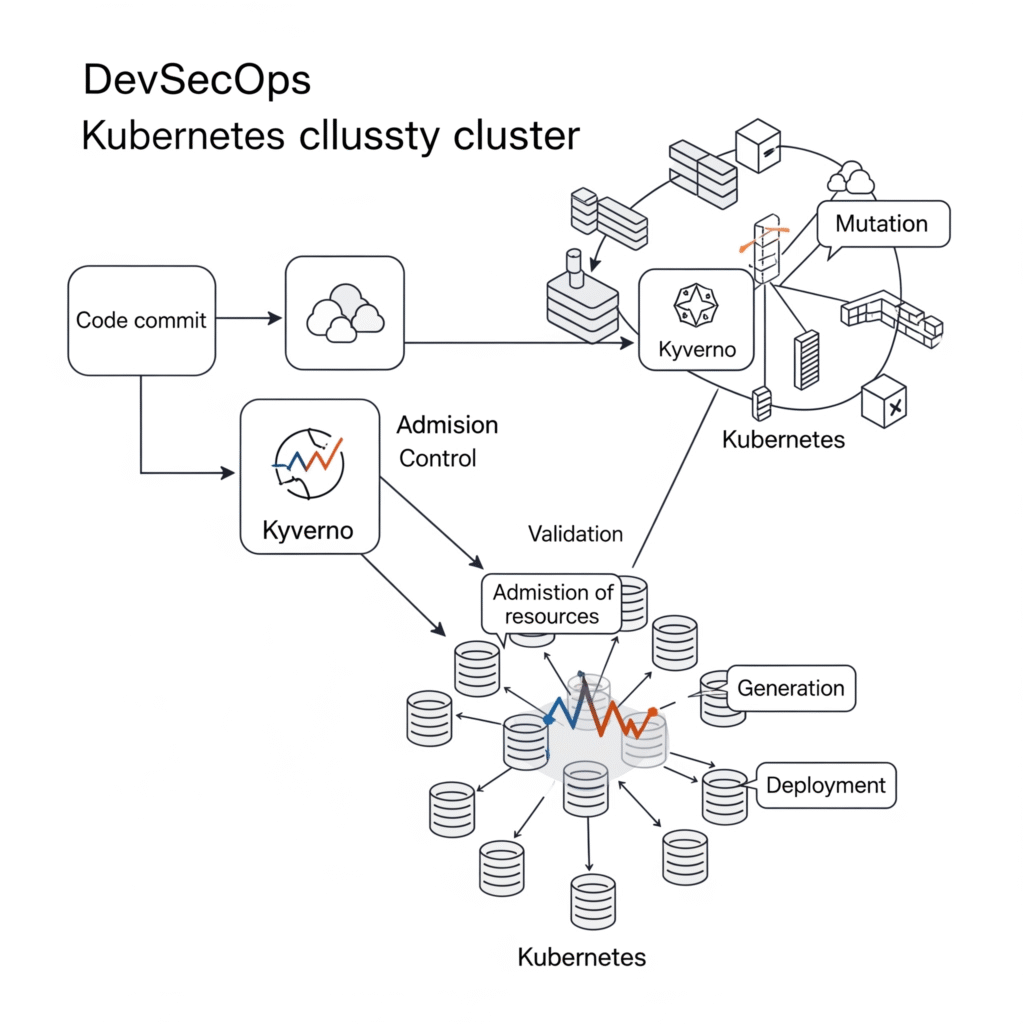
Workflow:
- The Kubernetes API server sends an AdmissionReview request to Kyverno’s webhook server when a resource is created, updated, or deleted.
- The policy engine matches the resource against applicable policies using kind, name, or label selectors.
- For validation, Kyverno checks compliance and either allows or blocks the request.
- For mutation, it applies changes (e.g., JSON Patch or overlays).
- For generation, it creates new resources based on policy triggers.
- Results are returned to the API server, and policy violations are logged as Kubernetes events or reports.
Architecture Diagram Description
The Kyverno architecture can be visualized as a layered system:
- Top Layer: Kubernetes API server sends AdmissionReview requests.
- Middle Layer: Kyverno’s webhook server receives requests, with the Webhook Controller configuring webhook rules dynamically.
- Core Layer: The Policy Engine processes requests, interacting with controllers (Background, Report, Cert Renewer).
- Bottom Layer: Kubernetes resources (Policies, CRDs, Secrets) store configurations and certificates.
- Output: Policy reports and Kubernetes events provide visibility into compliance and enforcement.
+----------------+ +---------------------+ +-------------------+
| K8s API Server | <---> | Kyverno Webhook| <--> | Kyverno Controller|
+----------------+ +---------------------+ +-------------------+
| |
+-----v-----+ +------v------+
| Policy | | Background |
| Evaluation| | Processing |
+-----------+ +-------------+Integration Points with CI/CD or Cloud Tools
Kyverno integrates seamlessly with:
- CI/CD Pipelines: The Kyverno CLI validates manifests in tools like Jenkins, GitLab CI, or GitHub Actions.
- GitOps: Policies are managed as code using Git, Kustomize, or Helm.
- Cloud Platforms: Supports AWS, Azure, and GCP by enforcing cloud-specific policies (e.g., IAM roles).
- Security Tools: Integrates with image scanners (e.g., Trivy) for software supply chain security.
Installation & Getting Started
Basic Setup or Prerequisites
- Kubernetes Cluster: Version 1.16 or higher (e.g., Minikube, Kind, or a cloud provider).
- kubectl: Installed and configured to interact with the cluster.
- Helm: Optional, for Helm-based installation.
- Permissions: Cluster-admin access to create namespaces and CRDs.
- Network: Ensure no network policies block Kyverno’s webhook communication.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide installs Kyverno using a manifest for simplicity. For production, Helm is recommended.
- Install via Helm:
helm repo add kyverno https://kyverno.github.io/kyverno/
helm repo update
helm install kyverno kyverno/kyverno -n kyverno --create-namespace- Verify Installation:
kubectl get pods -n kyverno- Apply a Sample Policy:
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: require-labels
spec:
validationFailureAction: enforce
rules:
- name: check-labels
match:
resources:
kinds:
- Pod
validate:
message: "All pods must have 'app' and 'env' labels."
pattern:
metadata:
labels:
app: "*"
env: "*"Apply with:
kubectl apply -f require-labels.yamlReal-World Use Cases
1. Enforcing Resource Limits
Ensure all deployments define CPU/memory limits:
validate:
message: "Resource limits are required."
pattern:
spec:
containers:
- resources:
limits:
memory: "*"
cpu: "*"2. Blocking Privileged Containers
Prevent the use of privileged containers for compliance:
validate:
message: "Privileged mode is not allowed."
pattern:
spec:
containers:
- securityContext:
privileged: false3. Auto-injecting Sidecars
Automatically add security sidecars to certain deployments.
4. Industry-specific Compliance
- Finance: Enforce PCI-DSS configurations like encrypted volumes.
- Healthcare: Require audit logging for HIPAA compliance.
Benefits & Limitations
Key Advantages
- Kubernetes-Native: Uses YAML and CRDs, eliminating the need for new languages like Rego.
- Automation: Supports validation, mutation, generation, and cleanup, reducing manual intervention.
- Flexibility: Policies apply to any Kubernetes resource or JSON payload.
- Community Support: CNCF Incubating project with a strong community and policy library.
Common Challenges or Limitations
- Kubernetes-Centric: Limited to Kubernetes environments, unlike general-purpose tools like OPA.
- Complexity in Large Clusters: Managing numerous policies can impact performance.
- Learning Curve for Advanced Features: Features like JMESPath expressions require additional expertise.
- Dependency Risks: Relies on Kubernetes admission controllers, which may introduce latency.
Best Practices & Recommendations
- Start with Audit Mode: Use
validationFailureAction: Auditto test policies without blocking resources. - Organize Policies: Use namespaces and clear naming conventions (e.g.,
require-labels,restrict-images). - Secure Kyverno: Apply RBAC to restrict policy creation and monitor webhook certificates.
- Automate Policy Testing: Integrate Kyverno CLI into CI/CD pipelines for early validation.
- Monitor Compliance: Regularly review policy reports and integrate with observability tools.
- Compliance Alignment: Map policies to standards like CIS Kubernetes Benchmarks or NIST 800-53.
Comparison with Alternatives
| Feature/Tool | Kyverno | Open Policy Agent (OPA) | Gatekeeper |
|---|---|---|---|
| Policy Language | Kubernetes YAML | Rego | Rego |
| Kubernetes-Native | Yes | No | Yes |
| Ease of Use | High (no new language) | Medium (Rego learning curve) | Medium |
| Use Cases | Kubernetes-specific | General-purpose | Kubernetes-specific |
| Performance | Optimized for Kubernetes | Flexible but complex | Moderate |
| Community | CNCF Incubating | CNCF Graduated | CNCF Incubating |
When to Choose Kyverno:
- Choose Kyverno for Kubernetes-native policy management with minimal learning curve.
- Use OPA for non-Kubernetes environments or complex policy logic.
- Opt for Gatekeeper when integrating OPA with Kubernetes but needing simpler Rego-based policies.
Conclusion
Kyverno is a powerful, Kubernetes-native policy engine that enhances DevSecOps by automating security, compliance, and best practices in the SDLC. Its ease of use, integration with CI/CD pipelines, and support for real-time policy enforcement make it ideal for securing cloud-native applications. While it excels in Kubernetes environments, its limitations in non-Kubernetes contexts highlight the need to evaluate use cases carefully. As cloud-native adoption grows, Kyverno’s role in policy-as-code will likely expand, with features like enhanced observability and broader ecosystem integration on the horizon.