Introduction & Overview
The Common Vulnerability Scoring System (CVSS) is a standardized framework for assessing the severity of security vulnerabilities in software and systems. In the fast-paced world of DevSecOps, where security is integrated into every phase of the software development lifecycle (SDLC), CVSS plays a critical role in prioritizing vulnerabilities and enabling teams to make informed risk-based decisions. This tutorial provides an in-depth exploration of CVSS, its architecture, integration with DevSecOps workflows, practical setup, use cases, benefits, limitations, and best practices.
What is CVSS (Common Vulnerability Scoring System)?
CVSS is an open, industry-standard method for rating the severity of security vulnerabilities. It provides a numerical score (0–10) to reflect the potential impact and exploitability of a vulnerability, helping organizations prioritize remediation efforts.
- Purpose: Standardizes vulnerability assessment across tools, teams, and industries.
- Developed by: Forum of Incident Response and Security Teams (FIRST).
- Latest Version: CVSS v4.0 (released November 2023), with v3.1 still widely used.

History or Background
CVSS was first introduced in 2005 by FIRST to address the need for a consistent way to evaluate vulnerabilities. Its evolution includes:
- CVSS v1 (2005): Initial framework, limited in scope and flexibility.
- CVSS v2 (2007): Improved metrics and scoring for better granularity.
- CVSS v3.0/v3.1 (2015/2019): Enhanced focus on exploitability and impact, widely adopted.
- CVSS v4.0 (2023): Introduced refined metrics, including safety impact and automation potential.
Why is it Relevant in DevSecOps?
In DevSecOps, security is a shared responsibility across development, security, and operations teams. CVSS is critical because it:
- Prioritizes Risks: Helps teams focus on high-severity vulnerabilities in CI/CD pipelines.
- Enables Automation: Integrates with vulnerability scanners and DevSecOps tools for automated prioritization.
- Supports Compliance: Aligns with standards like NIST, PCI DSS, and ISO 27001.
- Facilitates Collaboration: Provides a common language for developers, security analysts, and operations teams.
Core Concepts & Terminology
Key Terms and Definitions
- Base Score: Represents the inherent severity of a vulnerability (0–10), based on exploitability and impact.
- Temporal Score: Adjusts the base score with time-sensitive factors like exploit availability or patch status.
- Environmental Score: Customizes the score based on an organization’s specific environment (e.g., asset criticality).
- Attack Vector (AV): How a vulnerability can be exploited (e.g., network, local).
- Attack Complexity (AC): The difficulty of exploiting the vulnerability.
- Impact Metrics: Confidentiality, Integrity, Availability (CIA) triad impacts.
- CVSS Vector String: A compact representation of metrics (e.g.,
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
| Term | Definition |
|---|---|
| Base Score | Represents the intrinsic and fundamental characteristics of a vulnerability |
| Temporal Score | Considers factors that change over time (e.g., exploit availability) |
| Environmental Score | Accounts for specific configurations and environments |
| Attack Vector (AV) | Describes how the vulnerability can be exploited (e.g., network, local) |
| Attack Complexity (AC) | The conditions beyond the attacker’s control required to exploit |
| Privileges Required (PR) | Level of privileges required by an attacker |
| User Interaction (UI) | Indicates whether user action is required |
How it Fits into the DevSecOps Lifecycle
CVSS integrates across the DevSecOps lifecycle:
- Plan & Code: Identify vulnerabilities in libraries using tools like Dependabot, which leverage CVSS scores.
- Build & Test: Static Application Security Testing (SAST) tools like Snyk use CVSS to flag high-risk issues.
- Release & Deploy: Dynamic Application Security Testing (DAST) and Infrastructure as Code (IaC) scanning incorporate CVSS for prioritization.
- Operate & Monitor: Security Information and Event Management (SIEM) systems use CVSS to monitor and respond to vulnerabilities.
| DevSecOps Stage | Role of CVSS |
|---|---|
| Plan | Define security policies based on CVSS thresholds |
| Develop | Embed CVSS-based gates in pull request validation |
| Build/Test | Automated scans report CVSS scores |
| Release | Block releases on high CVSS score vulnerabilities |
| Operate/Monitor | Continuous monitoring and alerting |
Architecture & How It Works
Components & Internal Workflow
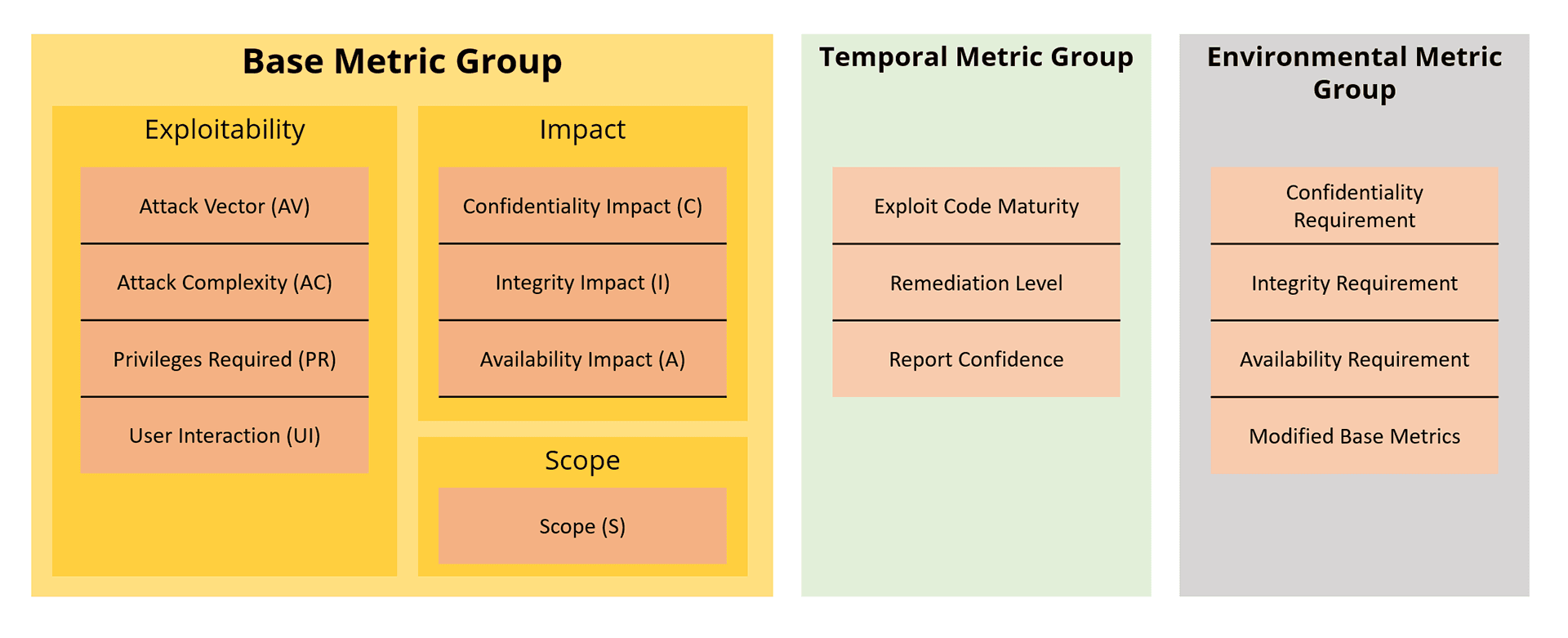
CVSS consists of three metric groups:
- Base Metrics: Intrinsic characteristics of a vulnerability.
- Exploitability: Attack Vector, Attack Complexity, Privileges Required, User Interaction.
- Impact: Confidentiality, Integrity, Availability.
- Temporal Metrics: Time-dependent factors (e.g., exploit code maturity, remediation level).
- Environmental Metrics: Organization-specific factors (e.g., modified base metrics, security requirements).
The workflow involves:
- Vulnerability Identification: Tools like Nessus or Qualys detect vulnerabilities and assign CVSS scores.
- Scoring: Analysts or tools calculate the Base Score, optionally adjusting with Temporal and Environmental metrics.
- Prioritization: Teams use the final score to prioritize remediation in the DevSecOps pipeline.
Architecture Diagram (Text Description)
Imagine a flowchart with:
- Input: Vulnerability data from scanners (e.g., CVE-2023-1234).
- Processing: CVSS calculator (e.g., FIRST’s online tool or API) evaluates Base, Temporal, and Environmental metrics.
- Output: A CVSS score and vector string fed into DevSecOps tools (e.g., Jenkins, GitLab).
- Integration: CI/CD pipelines, ticketing systems (e.g., Jira), or SIEM platforms consume the score for action.
Integration Points with CI/CD or Cloud Tools
- CI/CD Pipelines: Tools like Jenkins or GitLab CI integrate CVSS via plugins (e.g., OWASP Dependency-Check).
- Cloud Security: AWS Security Hub and Azure Defender use CVSS to prioritize vulnerabilities in cloud workloads.
- Container Security: Tools like Trivy or Clair embed CVSS scores for container image vulnerabilities.
- APIs: CVSS data can be queried via NVD (National Vulnerability Database) APIs for real-time integration.
Installation & Getting Started
Basic Setup or Prerequisites
To use CVSS in a DevSecOps environment, you need:
- A vulnerability scanner (e.g., Nessus, OpenVAS, Snyk).
- Access to the NVD API or CVE database for CVSS scores.
- A CI/CD pipeline (e.g., Jenkins, GitLab).
- Basic knowledge of vulnerability management and JSON/XML parsing.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
Let’s set up a simple Python script to fetch and parse CVSS scores from the NVD API and integrate them into a DevSecOps workflow.
- Install Dependencies:
pip install requests 2. Fetch CVSS Data:
Create a Python script to query the NVD API for a CVE’s CVSS score.
import requests
def get_cvss_score(cve_id):
url = f"https://services.nvd.nist.gov/rest/json/cve/1.0/{cve_id}"
response = requests.get(url)
if response.status_code == 200:
data = response.json()
cvss_v3 = data['result']['CVE_Items'][0]['metrics']['cvssMetricV31'][0]['cvssData']
score = cvss_v3['baseScore']
vector = cvss_v3['vectorString']
return score, vector
return None, None
cve_id = "CVE-2023-1234"
score, vector = get_cvss_score(cve_id)
print(f"CVSS Score: {score}, Vector: {vector}")3. Integrate with CI/CD:
Add the script to a GitLab CI pipeline to check vulnerabilities in a repository.
stages:
- security
vulnerability_check:
stage: security
script:
- pip install requests
- python cvss_check.py
artifacts:
paths:
- cvss_report.txt4. Run and Review:
- Push the code to your repository.
- The pipeline runs the script and outputs CVSS scores to
cvss_report.txt.
Real-World Use Cases
- Dependency Scanning in CI/CD:
- Scenario: A DevSecOps team uses Snyk to scan Node.js dependencies in a GitHub repository. A library with CVE-2023-1234 has a CVSS score of 9.8 (Critical). The team prioritizes upgrading the library before deployment.
- Industry: FinTech, where high-severity vulnerabilities could lead to data breaches.
- Container Security in Kubernetes:
- Scenario: A cloud-native application uses Docker images scanned by Trivy. A base image vulnerability (CVE-2022-5678, CVSS 7.5) is flagged. The team rebuilds the image with a patched version.
- Industry: E-commerce, ensuring secure container deployments.
- Cloud Infrastructure Misconfiguration:
- Scenario: AWS Security Hub identifies an exposed S3 bucket vulnerability (CVSS 8.1). The DevSecOps team automates a Lambda function to restrict bucket access based on the CVSS score.
- Industry: Healthcare, aligning with HIPAA compliance.
- Incident Response Prioritization:
- Scenario: A SIEM tool (e.g., Splunk) flags a critical vulnerability in a production server (CVSS 9.0). The operations team uses the CVSS score to prioritize patching during a maintenance window.
- Industry: Government, ensuring rapid response to critical threats.
Benefits & Limitations
Key Advantages
- Standardization: Universally accepted scoring system for consistent vulnerability assessment.
- Prioritization: Helps focus on high-impact vulnerabilities, reducing risk exposure.
- Integration: Seamlessly works with DevSecOps tools like Snyk, Qualys, and AWS Security Hub.
- Flexibility: Environmental metrics allow customization for specific organizational needs.
Common Challenges or Limitations
- Context Dependency: CVSS scores may not fully reflect an organization’s unique environment without Environmental metrics.
- Static Nature: Scores don’t account for real-time changes in exploitability unless updated.
- Complexity: Calculating Temporal and Environmental scores requires expertise.
- Over-Reliance: Teams may focus solely on high CVSS scores, ignoring low-scoring but exploitable vulnerabilities.
Best Practices & Recommendations
- Automate Scoring: Use tools like Snyk or Qualys to automate CVSS score retrieval in CI/CD pipelines.
- Customize Environmental Metrics: Tailor scores to reflect asset criticality (e.g., production vs. development servers).
- Combine with Other Metrics: Use CVSS alongside threat intelligence and exploitability data for holistic prioritization.
- Compliance Alignment: Map CVSS scores to compliance requirements (e.g., PCI DSS mandates addressing CVSS ≥ 7.0).
- Regular Updates: Monitor NVD for updated CVSS scores as new exploits or patches emerge.
- Training: Educate DevSecOps teams on interpreting CVSS vector strings and scores.
Comparison with Alternatives
| Feature | CVSS | EPSS (Exploit Prediction Scoring System) | OWASP Risk Rating |
|---|---|---|---|
| Purpose | Severity scoring for vulnerabilities | Predicts likelihood of exploitation | Risk-based assessment |
| Scoring Range | 0–10 | 0–1 (probability) | Qualitative (Low–Critical) |
| Standardization | Industry standard (FIRST) | Emerging standard (FIRST) | OWASP-specific |
| DevSecOps Integration | High (CI/CD, scanners) | Moderate (limited tool support) | Low (manual process) |
| Use Case | Prioritize remediation | Predict active exploitation | Risk analysis |
When to Choose CVSS
- Choose CVSS: For standardized, automated vulnerability prioritization in DevSecOps pipelines.
- Choose Alternatives: Use EPSS for exploit likelihood or OWASP Risk Rating for qualitative risk assessments when CVSS lacks context.
Conclusion
CVSS is a cornerstone of vulnerability management in DevSecOps, providing a standardized, quantifiable way to prioritize security risks. By integrating CVSS into CI/CD pipelines, cloud security tools, and incident response workflows, teams can enhance security while maintaining development velocity. Future trends include greater automation of CVSS scoring, integration with AI-driven threat intelligence, and adoption of CVSS v4.0 for more granular metrics.
Next Steps
- Explore CVSS v4.0 specifications for advanced metrics.
- Experiment with tools like Snyk or Trivy to integrate CVSS into your workflows.
- Join communities like FIRST for updates on CVSS standards.