
Introduction & Overview
Dynamic Application Security Testing (DAST) is a critical practice in modern software development, particularly within the DevSecOps framework, where security is seamlessly integrated into the development and operations lifecycle. This tutorial provides an in-depth exploration of DAST, its role in DevSecOps, and practical guidance for implementation. Designed for developers, security professionals, and DevSecOps practitioners, this guide covers core concepts, setup, use cases, and best practices to help you leverage DAST effectively.
What is DAST (Dynamic Application Security Testing)?
DAST is a security testing methodology that analyzes a running application to identify vulnerabilities by simulating external attacks. Unlike Static Application Security Testing (SAST), which examines source code, DAST interacts with the application’s runtime environment (e.g., via HTTP requests) to detect issues like SQL injection, cross-site scripting (XSS), and authentication flaws.
- Key Characteristics:
- Tests applications in a live or staged environment.
- Does not require access to source code (black-box testing).
- Focuses on exploitable vulnerabilities from an attacker’s perspective.
History or Background
DAST emerged in the early 2000s as web applications became prevalent and traditional security testing methods proved insufficient for dynamic, internet-facing systems. Tools like Burp Suite and OWASP ZAP popularized DAST by automating vulnerability scanning. With the rise of DevSecOps in the 2010s, DAST became integral to continuous integration and delivery pipelines, enabling automated security testing at scale.
Why is it Relevant in DevSecOps?
DevSecOps emphasizes “shifting left” to integrate security early and often in the software development lifecycle (SDLC). DAST complements this by:
- Automating Security Testing: Integrates with CI/CD pipelines to catch vulnerabilities before deployment.
- Real-World Attack Simulation: Mimics how attackers exploit running applications.
- Compliance Support: Helps meet standards like PCI-DSS, HIPAA, and GDPR by identifying runtime vulnerabilities.
- Scalability: Adapts to cloud-native and microservices architectures.
Core Concepts & Terminology
Key Terms and Definitions
- DAST: Dynamic Application Security Testing; tests running applications for vulnerabilities.
- Black-Box Testing: Testing without knowledge of the application’s internal code or structure.
- Vulnerability: A weakness that can be exploited, e.g., XSS, SQL injection.
- Crawler: A DAST tool component that maps an application’s structure by navigating its pages and APIs.
- Attack Simulation: Automated or manual techniques to mimic real-world attacks.
- False Positive/Negative: Incorrectly identified or missed vulnerabilities.
How It Fits into the DevSecOps Lifecycle
DAST integrates into the SDLC at multiple stages:
- Development: Tests prototypes or staging environments to catch issues early.
- Build: Runs automated scans during CI/CD to validate builds.
- Deployment: Verifies production-like environments before release.
- Monitoring: Continuously scans live applications for new vulnerabilities.
DAST complements SAST and Interactive Application Security Testing (IAST) by focusing on runtime behavior, ensuring a comprehensive security posture.
Architecture & How It Works
Components and Internal Workflow
DAST tools typically consist of:
- Crawler/Spider: Discovers application endpoints (e.g., URLs, APIs) by navigating the application.
- Scanner: Sends malicious inputs to test for vulnerabilities like XSS, SQL injection, or insecure configurations.
- Reporting Engine: Generates detailed reports with findings, severity, and remediation steps.
- Integration Layer: Connects with CI/CD tools (e.g., Jenkins, GitLab) or cloud platforms (e.g., AWS, Azure).
Workflow:
- Discovery: The crawler maps the application’s attack surface (e.g., forms, APIs).
- Attack Simulation: The scanner sends payloads to test for vulnerabilities.
- Analysis: The tool evaluates responses to identify exploitable issues.
- Reporting: Results are compiled with details on vulnerabilities, severity, and fixes.
Architecture Diagram Description
Imagine a diagram with the following components:
- Central DAST Engine: A box labeled “DAST Tool” containing sub-boxes for Crawler, Scanner, and Reporting Engine.
- Application Under Test: A web app icon (e.g., a browser) connected to the DAST Engine via HTTP/HTTPS.
- CI/CD Pipeline: A horizontal pipeline (Code → Build → Test → Deploy) with the DAST Tool integrated at the Test stage.
- Cloud Integration: Icons for AWS, Azure, or GitLab connected to the DAST Engine via APIs.
- Output: A report icon with vulnerability details flowing from the DAST Engine.
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration:
- Jenkins: Plugins like OWASP ZAP or Burp Suite integrate DAST scans into build pipelines.
- GitLab/GitHub Actions: YAML configurations trigger DAST scans on code commits.
- Cloud Tools:
- AWS: Integrates with AWS CodePipeline for automated testing.
- Azure DevOps: Uses tasks to run DAST tools like Netsparker.
- Kubernetes: Scans containerized applications in staging environments.
Installation & Getting Started
Basic Setup or Prerequisites
To set up a DAST tool like OWASP ZAP (open-source and beginner-friendly):
- Hardware: Minimum 4GB RAM, 2-core CPU.
- Software: Java 8+ (for OWASP ZAP), Docker (optional), or a cloud-based DAST service.
- Network: Access to the target application’s URL or staging environment.
- Permissions: Authentication credentials for the application (if required).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide uses OWASP ZAP on a local machine to scan a sample web application.
- Install OWASP ZAP:
- Download from https://www.zaproxy.org/.
- For Windows/Mac/Linux, run the installer or use Docker:
docker pull owasp/zap2docker-stable
- Launch OWASP ZAP:
- Run the desktop application or start the Docker container:
docker run -u zap -p 8080:8080 -i owasp/zap2docker-stable zap.sh -daemon -host 0.0.0.0 -port 8080
- Run the desktop application or start the Docker container:
- Configure the Target:
- Open ZAP’s UI (http://localhost:8080) or use the API.
- Set the target URL (e.g., http://testphp.vulnweb.com, a test application).
- Run a Spider Scan:
- In ZAP’s UI, go to “Quick Start” → Enter URL → Click “Attack”.
- Alternatively, use the API:
curl "http://localhost:8080/JSON/spider/action/scan/?url=http://testphp.vulnweb.com"
- Run an Active Scan:
- In the UI, select “Active Scan” to test for vulnerabilities.
- Via API:
curl "http://localhost:8080/JSON/ascan/action/scan/?url=http://testphp.vulnweb.com"
- View Results:
- Check the “Alerts” tab for vulnerabilities (e.g., XSS, SQL injection).
- Export reports in HTML/PDF via the UI or API.
Real-World Use Cases
DAST is applied across industries to secure applications in DevSecOps pipelines. Below are four scenarios:
- E-Commerce Platform:
- Scenario: An online retailer uses DAST to scan its checkout process for vulnerabilities like session hijacking or XSS.
- Implementation: OWASP ZAP scans the staging environment during CI/CD, integrated with Jenkins.
- Outcome: Identifies insecure form inputs, enabling developers to fix issues before production.
- Healthcare Application (HIPAA Compliance):
- Scenario: A telemedicine app must comply with HIPAA by securing patient data.
- Implementation: Burp Suite scans APIs for improper authentication or data exposure.
- Outcome: Ensures compliance by detecting vulnerabilities in API endpoints.
- Financial Services (PCI-DSS):
- Scenario: A banking app requires PCI-DSS compliance for payment processing.
- Implementation: Netsparker scans the app in a Kubernetes cluster, integrated with Azure DevOps.
- Outcome: Detects SQL injection risks, ensuring secure transactions.
- SaaS Provider:
- Scenario: A SaaS company scans its multi-tenant application for cross-tenant data leaks.
- Implementation: Qualys DAST runs continuous scans in production, integrated with AWS CodePipeline.
- Outcome: Identifies misconfigured access controls, preventing data breaches.
Benefits & Limitations
Key Advantages
- No Source Code Required: Ideal for third-party or legacy applications.
- Real-World Testing: Simulates actual attacks, catching runtime-specific issues.
- CI/CD Integration: Automates security testing in DevSecOps pipelines.
- Compliance Support: Aligns with standards like PCI-DSS, GDPR, and HIPAA.
Common Challenges or Limitations
- False Positives: May report non-exploitable issues, requiring manual verification.
- Performance Overhead: Active scans can slow down applications or require dedicated environments.
- Limited Coverage: Misses code-level issues (addressed by SAST).
- Authentication Challenges: Struggles with complex login flows without proper configuration.
Best Practices & Recommendations
- Security Tips:
- Configure authentication properly to ensure full application coverage.
- Use rate-limiting to avoid overwhelming the target application.
- Validate findings to reduce false positives.
- Performance:
- Run scans in staging environments to avoid production impact.
- Schedule scans during low-traffic periods.
- Maintenance:
- Update DAST tools regularly to include new vulnerability signatures.
- Monitor scan logs for errors or incomplete scans.
- Compliance Alignment:
- Map DAST findings to compliance requirements (e.g., OWASP Top 10 for PCI-DSS).
- Retain scan reports for audit purposes.
- Automation Ideas:
- Integrate DAST with CI/CD using plugins (e.g., OWASP ZAP Jenkins plugin).
- Use APIs to trigger scans on code commits or deployments.
Comparison with Alternatives
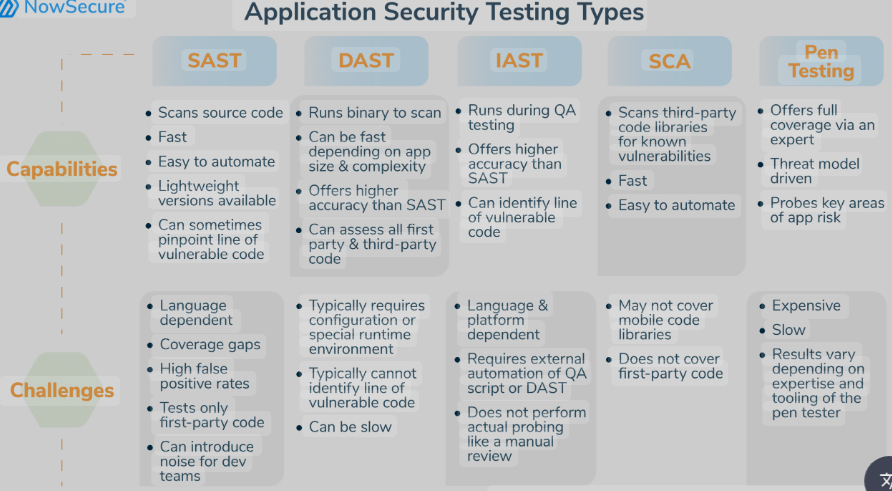
DAST is one of several security testing approaches. Below is a comparison with SAST and IAST:
| Aspect | DAST | SAST | IAST |
|---|---|---|---|
| Testing Approach | Black-box, runtime testing | White-box, code analysis | Hybrid, runtime with code insights |
| Source Code Access | Not required | Required | Optional |
| Stage in SDLC | Testing, deployment, monitoring | Coding, build | Testing, monitoring |
| Strengths | Finds runtime issues, compliance | Finds code-level flaws | Combines runtime and code insights |
| Weaknesses | False positives, no code visibility | Misses runtime issues | Complex setup, resource-intensive |
| Tools | OWASP ZAP, Burp Suite, Netsparker | SonarQube, Checkmarx | Contrast, Synopsys Seeker |
When to Choose DAST
- Use DAST When:
- Testing applications without source code access (e.g., third-party apps).
- Simulating real-world attacks in staging or production-like environments.
- Ensuring compliance with standards like PCI-DSS or GDPR.
- Choose Alternatives When:
- SAST: For early-stage code analysis or open-source projects.
- IAST: For applications requiring both runtime and code-level insights.
Conclusion
DAST is a cornerstone of DevSecOps, enabling teams to secure applications by simulating real-world attacks and integrating seamlessly with CI/CD pipelines. Its ability to test running applications without source code makes it versatile for diverse use cases, from e-commerce to healthcare. While it has limitations like false positives and performance overhead, following best practices and combining DAST with SAST or IAST ensures a robust security posture.
Future Trends:
- AI-Driven DAST: Machine learning to reduce false positives and improve scan accuracy.
- Cloud-Native Focus: Enhanced support for microservices and serverless architectures.
- Zero Trust Integration: DAST aligning with zero trust principles for continuous verification.
Next Steps:
- Explore tools like OWASP ZAP or Burp Suite for hands-on experience.
- Integrate DAST into your CI/CD pipeline for automated testing.
- Stay updated with communities like OWASP or vendor-specific forums.