Introduction & Overview
In today’s rapidly evolving digital landscape, securing software development pipelines is paramount. DevSecOps integrates security practices into the DevOps lifecycle, ensuring that security is a shared responsibility across development, operations, and security teams. Intrusion Detection and Prevention Systems (IDS/IPS) play a critical role in this paradigm by monitoring, detecting, and mitigating threats in real time. This tutorial explores IDS/IPS in the context of DevSecOps, covering its concepts, architecture, setup, use cases, benefits, limitations, and best practices.
What is IDS/IPS (Intrusion Detection/Prevention System)?
An Intrusion Detection System (IDS) monitors network or system activities for malicious activities or policy violations, logging or alerting on suspicious events. An Intrusion Prevention System (IPS) extends IDS capabilities by actively blocking or mitigating detected threats. Together, IDS/IPS solutions provide robust security mechanisms to protect infrastructure, applications, and data.
History or Background
IDS/IPS systems emerged in the late 1980s as network security became a priority. Early IDS solutions, like the 1988 model proposed by Dorothy Denning, focused on anomaly detection. By the 1990s, commercial products like Snort (1998) introduced signature-based detection. IPS systems evolved in the early 2000s, adding prevention capabilities. In DevSecOps, IDS/IPS integrates with CI/CD pipelines and cloud environments to address modern threats like zero-day attacks and insider threats.
Why is it Relevant in DevSecOps?
DevSecOps emphasizes “shift-left” security, embedding safeguards early in the development lifecycle. IDS/IPS systems are relevant because they:
- Provide real-time threat detection and prevention, aligning with DevSecOps’ continuous monitoring goals.
- Protect CI/CD pipelines and cloud-native applications from vulnerabilities.
- Enable compliance with regulations (e.g., GDPR, HIPAA) through audit trails and threat mitigation.
- Support automation, reducing manual intervention in security workflows.
Core Concepts & Terminology
Key Terms and Definitions
- Signature-Based Detection: Matches network traffic against known attack patterns (signatures).
- Anomaly-Based Detection: Identifies deviations from normal behavior, useful for unknown threats.
- Network-Based IDS/IPS (NIDS/NIPS): Monitors network traffic for suspicious activities.
- Host-Based IDS/IPS (HIDS/HIPS): Monitors activities on individual hosts or servers.
- False Positive/Negative: Incorrectly identifying benign activity as malicious (false positive) or missing a threat (false negative).
- Policy Rules: Configurable rules defining what constitutes a threat or acceptable behavior.
| Term | Definition |
|---|---|
| Log Aggregation | Collection of log data from multiple sources. |
| Correlation Engine | Identifies patterns or related security events. |
| Alerting | Notification based on rule-based or anomaly-based triggers. |
| Dashboard | Visualization of security metrics and events. |
| Threat Intelligence | Integration of external threat data for context-aware detection. |
How It Fits into the DevSecOps Lifecycle
IDS/IPS integrates across the DevSecOps lifecycle:
- Plan: Define security policies and rules for IDS/IPS.
- Code: Scan code for vulnerabilities that IDS/IPS can monitor (e.g., SQL injection patterns).
- Build: Integrate IDS/IPS with CI tools to monitor build environments.
- Test: Use IDS/IPS to detect threats during testing phases.
- Deploy: Monitor production traffic for real-time threat detection.
- Operate/Monitor: Continuously analyze logs and update rules to adapt to new threats.
| Phase | SIEM Role |
|---|---|
| Plan | Define logging and monitoring requirements. |
| Develop | Embed logging libraries and structured output. |
| Build | Analyze build logs for anomalies. |
| Test | Monitor test environments for vulnerabilities. |
| Release | Validate configurations for audit readiness. |
| Deploy | Real-time monitoring of deployment events. |
| Operate | Alert on operational anomalies or breaches. |
| Monitor | Continuous behavioral analysis and incident response. |
Architecture & How It Works
Components and Internal Workflow
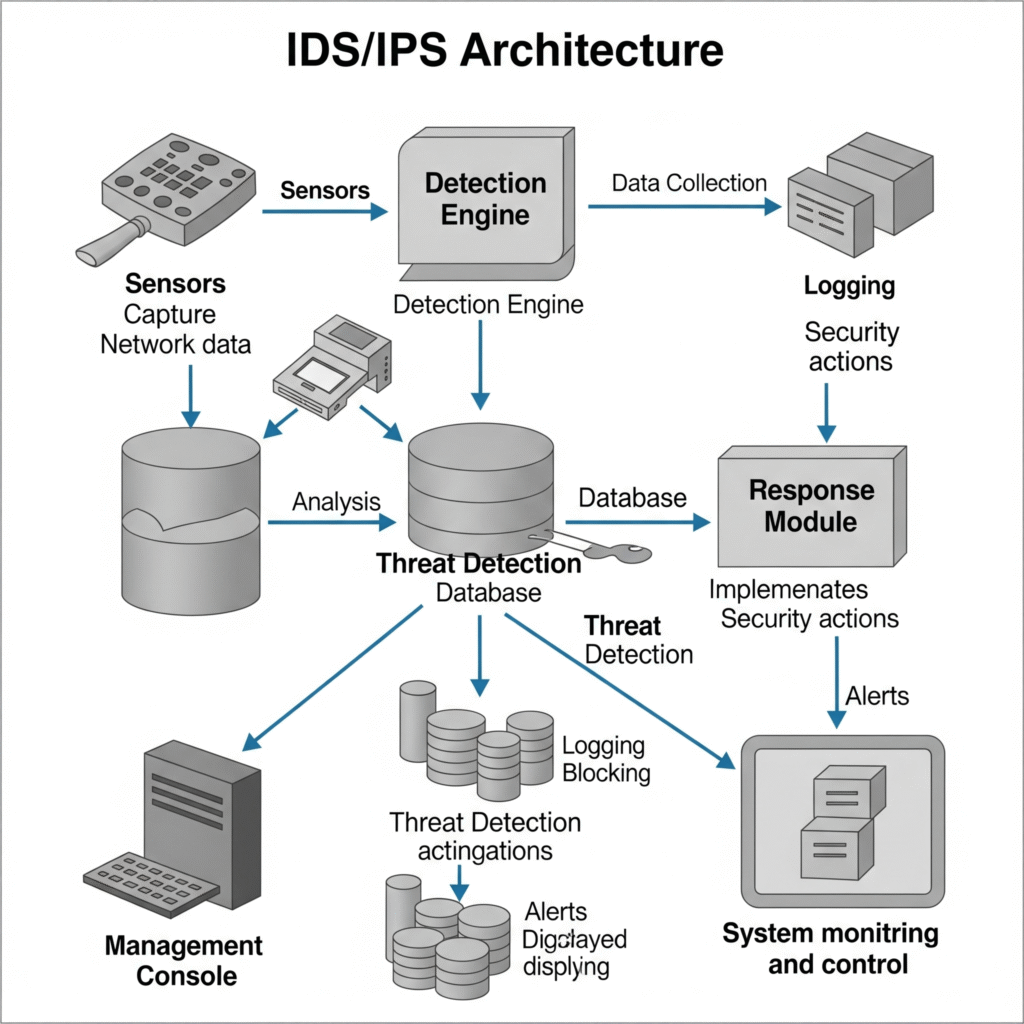
IDS/IPS systems typically include:
- Sensors: Capture network or host data (e.g., packets, logs).
- Detection Engine: Analyzes data using signature-based or anomaly-based methods.
- Database: Stores signatures, rules, and logs.
- Response Module: Generates alerts (IDS) or blocks threats (IPS).
- Management Console: Provides a UI for configuration, monitoring, and reporting.
Workflow:
- Sensors collect data (e.g., network packets, system logs).
- The detection engine analyzes data against rules or behavioral baselines.
- If a threat is detected, the system logs an alert (IDS) or blocks the activity (IPS).
- Alerts are sent to the management console or integrated systems (e.g., SIEM).
Architecture Description
Imagine a layered architecture:
- Data Layer: Network interfaces or host agents collect raw data.
- Processing Layer: A central engine processes data using predefined rules or machine learning models.
- Action Layer: Outputs include logs, alerts, or automated actions (e.g., dropping packets).
- Integration Layer: Connects to CI/CD tools (e.g., Jenkins), cloud platforms (e.g., AWS), or SIEM systems.
In a cloud-native DevSecOps environment, IDS/IPS might be deployed as a containerized service (e.g., Suricata in a Kubernetes cluster), with sensors distributed across nodes and a centralized console for monitoring.
[Endpoints/Apps/Cloud] --> [Data Collectors/Log Forwarders]
--> [Ingestion/Normalization]
--> [SIEM Data Store]
--> [Correlation & Detection Engine]
--> [Dashboards/Alerting/Reporting]
Integration Points with CI/CD or Cloud Tools
- CI/CD: Integrate with Jenkins or GitLab CI to monitor pipeline traffic for anomalies.
- Cloud: Use AWS GuardDuty or Azure Sentinel for cloud-native IDS/IPS.
- Container Security: Deploy IDS/IPS in Kubernetes to monitor pod-to-pod communication.
- SIEM Integration: Feed IDS/IPS logs into Splunk or ELK for centralized analysis.
Installation & Getting Started
Basic Setup or Prerequisites
To set up an open-source IDS/IPS like Snort:
- Hardware: A server with 4GB RAM, 2 CPUs, and 20GB storage.
- OS: Ubuntu 20.04 LTS or CentOS 8.
- Dependencies:
libpcap,pcre,g++,make. - Network: Access to network traffic (e.g., via a SPAN port or tap).
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide installs Snort on Ubuntu 20.04 as an IDS.
- Update System:
sudo apt update && sudo apt upgrade -y2. Install Dependencies:
sudo apt install -y build-essential libpcap-dev libpcre3-dev libdumbnet-dev bison flex zlib1g-dev3. Download and Install Snort:
wget https://www.snort.org/downloads/snort/snort-2.9.20.tar.gz tar -xvzf snort-2.9.20.tar.gz cd snort-2.9.20 ./configure --enable-sourcefire make sudo make install4. Configure Snort:
- Edit
/etc/snort/snort.conf:
sudo nano /etc/snort/snort.confSet the network range:
ipvar HOME_NET 192.168.1.0/24- Download community rules:
wget https://www.snort.org/downloads/community/community-rules.tar.gz tar -xvzf community-rules.tar.gz -C /etc/snort/rules5. Run Snort in IDS Mode:
sudo snort -c /etc/snort/snort.conf -i eth0 -A console Replace eth0 with your network interface.6. Verify Alerts:
- Simulate traffic (e.g., ping or HTTP requests).
- Check console output for alerts.
Real-World Use Cases
Scenario 1: Securing a CI/CD Pipeline
A DevSecOps team uses Snort to monitor Jenkins servers for unauthorized access. By deploying Snort in NIDS mode, the team detects SQL injection attempts targeting the Jenkins API, triggering alerts in a SIEM system for further analysis.
Scenario 2: Protecting Cloud-Native Applications
A company running Kubernetes on AWS uses Suricata as an IPS to monitor pod communication. Suricata blocks malicious traffic (e.g., DDoS attempts) by integrating with AWS Network Firewall, ensuring application uptime.
Scenario 3: Compliance in Healthcare
A healthcare provider uses HIDS (e.g., OSSEC) to monitor servers hosting patient data. The system detects unauthorized file changes, ensuring HIPAA compliance by logging and alerting on potential data breaches.
Scenario 4: E-Commerce Threat Detection
An e-commerce platform integrates Zeek (Bro) with its CI/CD pipeline to detect phishing attempts targeting customer login pages. Zeek’s anomaly detection identifies unusual login patterns, reducing fraud risk.
Benefits & Limitations
Key Advantages
- Real-Time Threat Detection: Identifies and responds to threats instantly.
- Automation: Integrates with CI/CD and cloud tools for automated responses.
- Compliance Support: Provides audit trails for regulatory requirements.
- Scalability: Works in on-premises, cloud, and hybrid environments.
Common Challenges or Limitations
- False Positives: May generate alerts for benign activities, requiring tuning.
- Resource Intensive: High traffic volumes can strain system resources.
- Complex Configuration: Requires expertise to define effective rules.
- Limited Zero-Day Protection: Signature-based systems struggle with unknown threats.
Best Practices & Recommendations
Security Tips
- Regularly update signatures and rules to address new threats.
- Use anomaly-based detection alongside signature-based for broader coverage.
- Encrypt IDS/IPS communications to prevent interception.
Performance
- Optimize rule sets to reduce false positives and processing overhead.
- Deploy on dedicated hardware or high-performance cloud instances.
Maintenance
- Monitor logs daily and integrate with SIEM for centralized analysis.
- Automate rule updates using scripts or tools like PulledPork.
Compliance Alignment
- Map IDS/IPS rules to compliance frameworks (e.g., PCI-DSS, GDPR).
- Retain logs for the required duration (e.g., 1 year for PCI-DSS).
Automation Ideas
- Integrate with Terraform for automated IDS/IPS deployment.
- Use Ansible to manage rule updates across multiple instances.
Comparison with Alternatives
| Tool/Approach | IDS/IPS | WAF (Web Application Firewall) | SIEM |
|---|---|---|---|
| Purpose | Detects/prevents network and host threats | Protects web applications from attacks | Aggregates and analyzes logs |
| Strengths | Real-time detection, prevention | Application-layer protection | Centralized log analysis |
| Weaknesses | Complex setup, false positives | Limited to web traffic | No prevention capabilities |
| Use Case | Network-wide threat monitoring | Web app security (e.g., SQL injection) | Compliance and forensics |
When to Choose IDS/IPS
- Choose IDS/IPS for network-wide or host-based monitoring.
- Use WAF for web-specific threats (e.g., XSS, CSRF).
- Opt for SIEM when centralized log analysis is needed.
Conclusion
IDS/IPS systems are indispensable in DevSecOps, offering real-time threat detection and prevention across the development lifecycle. By integrating with CI/CD pipelines and cloud environments, they enhance security without compromising agility. Future trends include AI-driven anomaly detection and tighter integration with cloud-native tools. To get started, explore open-source options like Snort or Suricata, and consider commercial solutions like Cisco Secure IPS for enterprise needs.