Introduction & Overview
Security Information and Event Management (SIEM) systems are critical for securing modern software development pipelines, particularly in DevSecOps, where security is integrated into every phase of the development lifecycle. This tutorial provides a detailed exploration of SIEM, its role in DevSecOps, and practical guidance for implementation.
What is SIEM?
SIEM combines Security Information Management (SIM) and Security Event Management (SEM) to provide real-time monitoring, analysis, and response to security events. It collects, aggregates, and analyzes log data from various sources to detect threats, ensure compliance, and support incident response.
History and Background
SIEM emerged in the early 2000s as organizations needed centralized solutions to manage growing volumes of security data. Early systems focused on log collection and compliance reporting. Modern SIEMs incorporate advanced analytics, machine learning, and integration with cloud-native tools, aligning with DevSecOps’ emphasis on automation and continuous monitoring.
Why is SIEM Relevant in DevSecOps?
DevSecOps integrates security into development and operations, emphasizing automation, collaboration, and continuous delivery. SIEM supports this by:
- Continuous Monitoring: Detecting threats across development, testing, and production environments.
- Automation: Enabling automated responses to security incidents in CI/CD pipelines.
- Compliance: Ensuring adherence to regulations like GDPR, HIPAA, or PCI-DSS.
- Collaboration: Providing a centralized platform for DevOps and security teams to share insights.
Core Concepts & Terminology
SIEM systems rely on specific concepts critical to understanding their role in DevSecOps:
- Log Aggregation: Collecting logs from applications, servers, networks, and cloud services.
- Correlation: Analyzing log data to identify patterns or anomalies indicating threats.
- Alerting: Notifying teams of potential security incidents based on predefined rules.
- Dashboard: Visual interface for real-time monitoring and reporting.
- Incident Response: Processes to investigate and mitigate detected threats.
| Term | Definition |
|---|---|
| Log Aggregation | Collection of log data from multiple sources. |
| Correlation Engine | Identifies patterns or related security events. |
| Alerting | Notification based on rule-based or anomaly-based triggers. |
| Dashboard | Visualization of security metrics and events. |
| Threat Intelligence | Integration of external threat data for context-aware detection. |
How SIEM Fits into the DevSecOps Lifecycle
SIEM integrates across the DevSecOps lifecycle:
- Plan: Defines logging requirements and compliance needs.
- Code: Monitors code repositories for unauthorized changes.
- Build: Detects vulnerabilities in build tools or dependencies.
- Test: Analyzes test environment logs for anomalies.
- Release/Deploy: Ensures secure deployment through real-time monitoring.
- Operate/Monitor: Provides ongoing threat detection and compliance reporting.
| Phase | SIEM Role |
|---|---|
| Plan | Define logging and monitoring requirements. |
| Develop | Embed logging libraries and structured output. |
| Build | Analyze build logs for anomalies. |
| Test | Monitor test environments for vulnerabilities. |
| Release | Validate configurations for audit readiness. |
| Deploy | Real-time monitoring of deployment events. |
| Operate | Alert on operational anomalies or breaches. |
| Monitor | Continuous behavioral analysis and incident response. |
Architecture & How It Works
A SIEM system comprises several components working together to secure DevSecOps pipelines:
- Data Collectors: Agents or connectors that gather logs from sources (e.g., servers, cloud services, CI/CD tools).
- Log Storage: Centralized database for storing and indexing log data.
- Analysis Engine: Processes logs using correlation rules and machine learning to detect threats.
- Alerting System: Generates notifications or triggers automated responses.
- Dashboard/Reporting: Visualizes data and provides compliance reports.
Internal Workflow
- Data Ingestion: Logs are collected from sources like AWS CloudTrail, Jenkins, or Kubernetes.
- Normalization: Logs are standardized for consistent analysis.
- Correlation: Rules or AI identify suspicious patterns (e.g., multiple failed login attempts).
- Alerting: Notifications are sent via email, Slack, or integrated ticketing systems.
- Response: Automated or manual actions mitigate threats.
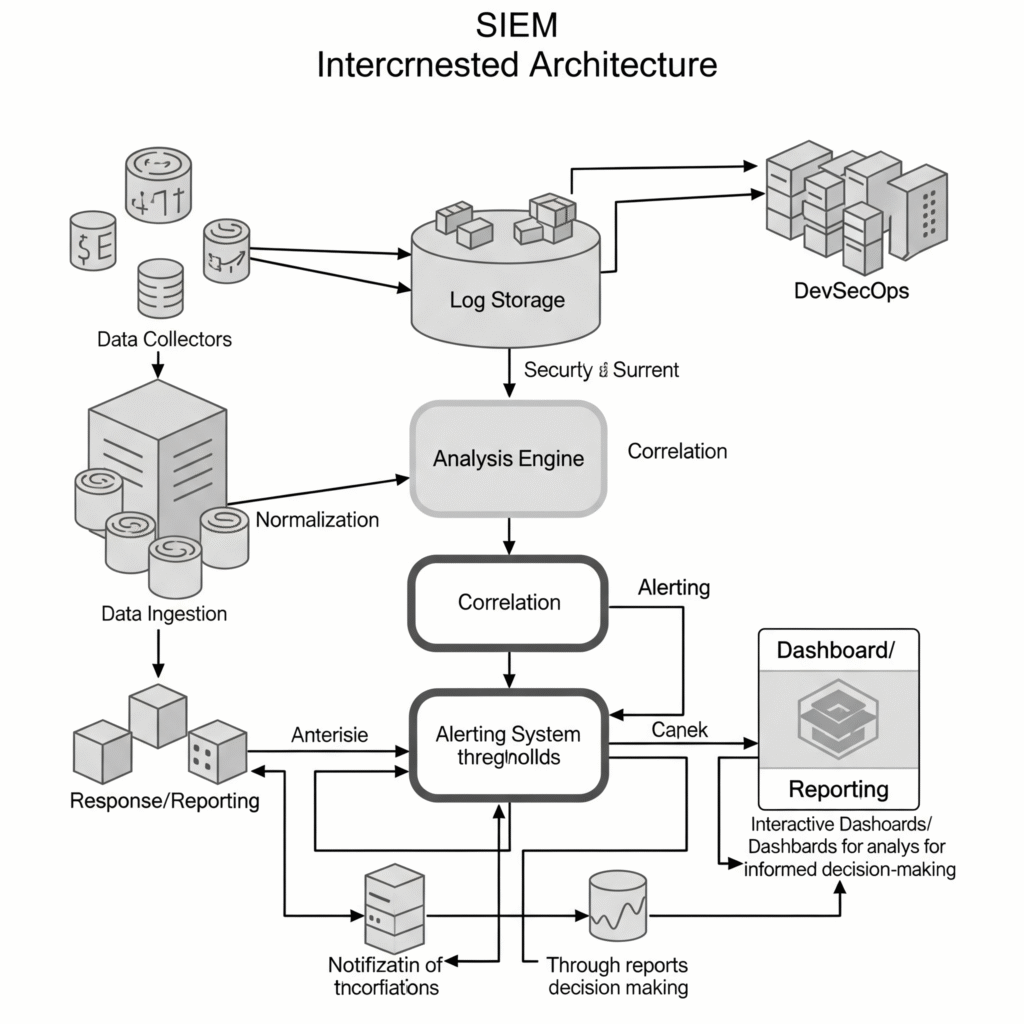
Architecture Diagram Description
The SIEM architecture can be visualized as a layered system:
- Top Layer: User interface (dashboards, reports).
- Middle Layer: Analysis engine and correlation rules.
- Bottom Layer: Data collectors and storage (e.g., Elasticsearch or Splunk database).
- Connections: Arrows show data flow from sources (e.g., CI/CD tools, cloud platforms) to collectors, then to storage and analysis.
[Endpoints/Apps/Cloud] --> [Data Collectors/Log Forwarders]
--> [Ingestion/Normalization]
--> [SIEM Data Store]
--> [Correlation & Detection Engine]
--> [Dashboards/Alerting/Reporting]
Integration with CI/CD and Cloud Tools
SIEM integrates with:
- CI/CD: Jenkins, GitLab, or CircleCI for monitoring pipeline events.
- Cloud: AWS, Azure, or GCP for collecting logs from cloud-native services.
- Container Platforms: Kubernetes or Docker for container security monitoring.
Example integration with AWS CloudTrail:
# Example AWS CLI command to enable CloudTrail logging
aws cloudtrail create-trail --name MyTrail --s3-bucket-name my-siem-bucketInstallation & Getting Started
This section guides you through setting up an open-source SIEM, Elastic Stack (ELK), for a DevSecOps environment.
Prerequisites
- System: Linux server (e.g., Ubuntu 20.04) with 8GB RAM, 4 CPUs.
- Software: Docker, Java 11, internet access.
- Access: Admin privileges for installation and configuration.
Step-by-Step Setup Guide
- Install Docker:
sudo apt update
sudo apt install -y docker.io
sudo systemctl start docker
sudo systemctl enable docker- Deploy Elastic Stack:
cat <<EOF > docker-compose.yml
version: '3'
services:
elasticsearch:
image: elasticsearch:8.10.0
environment:
- discovery.type=single-node
ports:
- "9200:9200"
kibana:
image: kibana:8.10.0
ports:
- "5601:5601"
depends_on:
- elasticsearch
EOF
docker-compose up -d- Configure Log Ingestion:
Install Filebeat to collect logs:
docker run -d --name filebeat --user root \
-v /var/log:/var/log:ro \
docker.elastic.co/beats/filebeat:8.10.0 \
filebeat -e -strict.perms=false- Access Kibana:
Open http://localhost:5601 in a browser, configure dashboards, and set up basic correlation rules.
Real-World Use Cases
SIEM is critical in various DevSecOps scenarios:
- Detecting Unauthorized Pipeline Access: Monitors CI/CD tools like Jenkins for unauthorized access attempts. Example: Alerts on repeated failed login attempts to a GitLab runner.
- Container Security: Tracks anomalies in Kubernetes clusters, such as unexpected pod terminations. Example: Identifies a pod running unauthorized code in a financial application.
- Cloud Misconfiguration: Detects misconfigured AWS S3 buckets via CloudTrail logs. Example: Alerts on public read access to sensitive data in a healthcare app.
- Compliance Monitoring: Ensures GDPR compliance by auditing access to personal data in a retail application.
Industry-Specific Example
In a financial services company, SIEM monitors payment processing systems for suspicious transactions, integrates with CI/CD pipelines to detect vulnerabilities in code, and generates compliance reports for PCI-DSS audits.
Benefits & Limitations
Key Advantages
- Centralized Visibility: Aggregates logs for a unified view of security events.
- Automation: Reduces manual effort in threat detection and response.
- Compliance: Simplifies adherence to regulatory standards.
- Scalability: Handles large-scale data from cloud and on-premises environments.
Common Challenges
- Complexity: Requires expertise to configure and maintain.
- Cost: Commercial SIEMs (e.g., Splunk) can be expensive.
- False Positives: May generate excessive alerts, requiring tuning.
- Data Volume: Large log volumes can strain storage and processing.
Best Practices & Recommendations
- Define Clear Rules: Create specific correlation rules to minimize false positives.
- Automate Responses: Use SOAR (Security Orchestration, Automation, and Response) tools to automate incident mitigation.
- Regular Maintenance: Update SIEM rules and integrations to reflect new threats.
- Compliance Alignment: Map SIEM reports to standards like ISO 27001 or NIST.
- Performance Optimization: Use distributed storage (e.g., Elasticsearch clusters) for scalability.
Comparison with Alternatives
| Criteria | SIEM | SOAR | Log Management |
|---|---|---|---|
| Primary Function | Threat detection | Incident response automation | Log storage |
| Real-Time Analysis | Yes | Limited | No |
| DevSecOps Integration | High | Medium | Low |
| Cost | High | Medium | Low |
| Use Case | Comprehensive monitoring | Automated workflows | Basic logging |
SIEM is one of several security monitoring approaches. Below is a comparison with alternatives:
When to Choose SIEM
Choose SIEM when you need:
- Real-time threat detection across diverse environments.
- Compliance reporting for regulated industries.
- Integration with CI/CD and cloud-native tools.
Opt for SOAR for automation-focused workflows or log management for simple log storage needs.
Conclusion
SIEM is a cornerstone of DevSecOps, enabling proactive security monitoring, compliance, and incident response. As DevSecOps evolves, SIEM systems are incorporating AI and automation to handle complex threats. Future trends include tighter integration with cloud-native platforms and enhanced machine learning for anomaly detection.