Introduction & Overview
Software Composition Analysis (SCA) is a critical practice in modern software development, particularly within DevSecOps, where security is integrated into the development lifecycle. This tutorial provides an in-depth exploration of SCA, its role in DevSecOps, and practical guidance for implementation. Designed for developers, security professionals, and DevSecOps practitioners, it covers core concepts, setup, real-world applications, and best practices.

What is SCA (Software Composition Analysis)?
SCA is an automated process for identifying, managing, and securing open-source and third-party components in software projects. It scans codebases to detect dependencies, libraries, and their associated vulnerabilities, licenses, and versions, ensuring compliance and security.
- Purpose: Mitigates risks from open-source software (OSS) by identifying vulnerabilities and ensuring license compliance.
- Scope: Covers libraries, frameworks, containers, and other external components.
History or Background
SCA emerged in the early 2000s as open-source software adoption surged. Early tools focused on license compliance, but with rising security threats (e.g., Heartbleed in 2014), SCA evolved to prioritize vulnerability detection.
- Key Milestones:
- 2003: Black Duck Software introduces early SCA tools for license management.
- 2010s: Integration with CI/CD pipelines becomes standard.
- 2020s: Cloud-native and container-focused SCA gains traction.
Why is it Relevant in DevSecOps?
DevSecOps emphasizes “shift-left” security, embedding security practices early in the development lifecycle. SCA aligns by:
- Proactive Security: Identifies vulnerabilities in dependencies before deployment.
- Automation: Integrates with CI/CD for continuous monitoring.
- Compliance: Ensures adherence to licensing and regulatory standards (e.g., GDPR, HIPAA).
Core Concepts & Terminology
Key Terms and Definitions
- Dependency: External libraries or packages used in a project (e.g., npm packages, Maven artifacts).
- Bill of Materials (BoM): A structured list of all components, versions, and licenses in a project.
- Vulnerability Database: Repositories like NVD (National Vulnerability Database) that SCA tools query.
- License Compliance: Ensuring OSS licenses align with project or organizational policies.
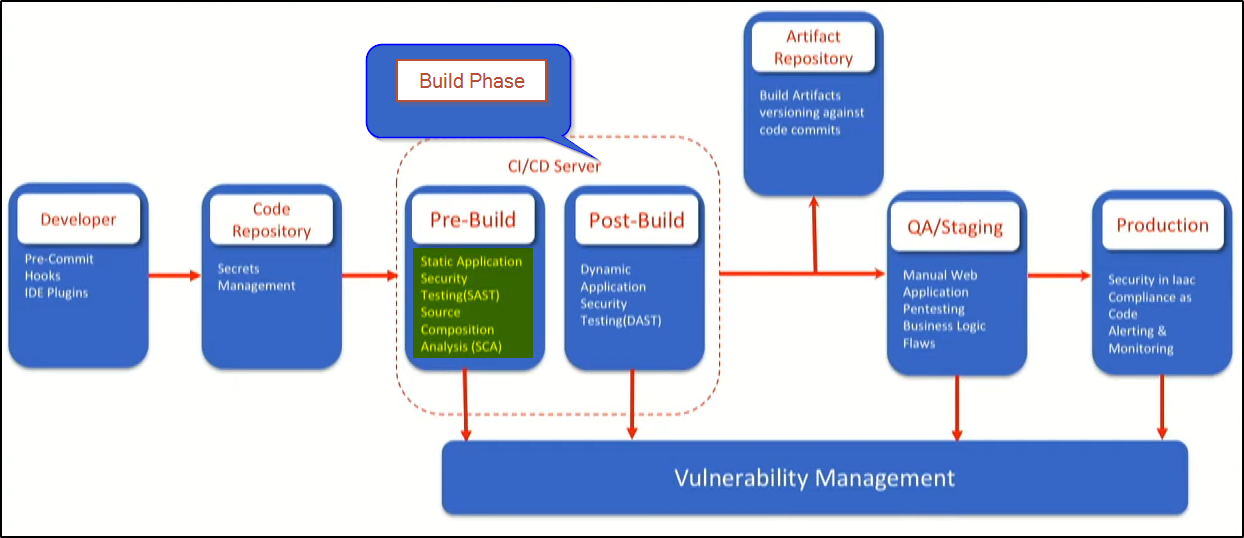
How It Fits into the DevSecOps Lifecycle
SCA integrates across DevSecOps phases:
- Plan: Identifies approved libraries and licenses.
- Code: Scans code repositories for vulnerabilities during development.
- Build: Integrates with CI tools to fail builds if critical issues are found.
- Deploy: Ensures containers and runtime environments are secure.
- Monitor: Continuously tracks new vulnerabilities in deployed components.
Architecture & How It Works
Components and Internal Workflow
SCA tools typically include:
- Scanner: Analyzes codebases, manifest files (e.g.,
pom.xml,package.json), or container images. - Database: Maintains a local or cloud-based vulnerability and license database.
- Policy Engine: Enforces rules (e.g., block builds with critical vulnerabilities).
- Reporting Module: Generates BoM and compliance reports.
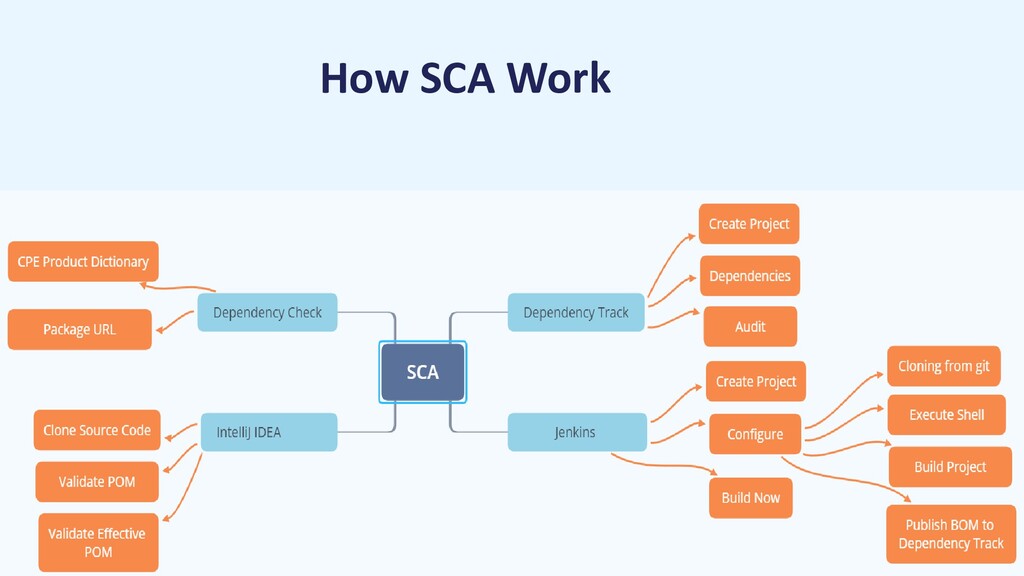
Workflow:
- Scan source code or binary artifacts to identify dependencies.
- Match components against vulnerability and license databases.
- Apply policies to flag issues (e.g., critical CVEs, non-compliant licenses).
- Generate reports and integrate results into CI/CD pipelines.
Architecture Diagram (Textual Description)
Imagine a flowchart with:
- Input: Source code, manifest files, or container images.
- SCA Tool: Central box with sub-components (Scanner, Database, Policy Engine, Reporting).
- Outputs: BoM, vulnerability reports, and CI/CD pipeline feedback.
- Connections: Bidirectional arrows to CI/CD tools (e.g., Jenkins, GitHub Actions), cloud platforms (e.g., AWS), and vulnerability databases (e.g., NVD).
Developer → SCM (GitHub, GitLab)
↓
SCA Triggered (on PR/Commit)
↓
┌──────────────────────────────┐
│ SCA Tool (e.g., Snyk) │
│ - Dependency Scanner │
│ - Vulnerability DB Lookup │
│ - Policy Evaluation │
└──────────────────────────────┘
↓
Report/Fail Build
↓
Dashboard / SBOM Output
Integration Points with CI/CD or Cloud Tools
- CI/CD: Plugins for Jenkins, GitHub Actions, or GitLab CI to scan during builds.
- Cloud: Integration with AWS CodePipeline, Azure DevOps, or Kubernetes for container scanning.
- IDEs: Plugins for VS Code or IntelliJ to provide real-time feedback.
Installation & Getting Started
Basic Setup or Prerequisites
To set up an SCA tool like Snyk or Dependabot:
- System Requirements: Node.js, Java, or Docker for tool-specific dependencies.
- Access: API tokens or credentials for repository access (e.g., GitHub, GitLab).
- Network: Access to vulnerability databases (e.g., NVD, OSS Index).
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
Let’s set up Snyk Open Source for a Node.js project.
- Install Snyk CLI:
npm install -g snyk2. Authenticate:
snyk authFollow the prompt to log in via browser and obtain an API token.
3. Navigate to Project:
cd /path/to/your/node-project4. Scan for Vulnerabilities:
snyk testThis scans package.json and reports vulnerabilities.
5. Integrate with GitHub:
- Go to snyk.io, connect your GitHub repository, and enable auto-scanning.
- Add a .snyk policy file to ignore low-severity issues:
ignore:
- '*':
- reason: "Low severity, will address later"
expires: 2025-12-316. View Results: Check the Snyk dashboard for a detailed BoM and remediation steps.
Real-World Use Cases
Scenario 1: E-commerce Platform
An e-commerce company uses SCA to secure its Node.js-based checkout system.
- Problem: Outdated
lodashlibrary with known vulnerabilities. - Solution: SCA tool flags the issue, suggests upgrading to
lodash@4.17.21, and blocks deployment until fixed. - Outcome: Prevents potential exploits during peak shopping seasons.
Scenario 2: Healthcare Application
A healthcare app must comply with HIPAA.
- Problem: Uses a library with a GPL license, risking compliance issues.
- Solution: SCA identifies the license conflict, and the team replaces it with an MIT-licensed alternative.
- Outcome: Ensures regulatory compliance and avoids legal risks.
Scenario 3: Containerized Microservices
A fintech firm deploys microservices in Docker containers.
- Problem: Base images contain outdated libraries with CVEs.
- Solution: SCA scans Dockerfiles and suggests updated base images.
- Outcome: Reduces attack surface in production.
Industry-Specific Example: Finance
Banks use SCA to monitor dependencies in trading platforms, ensuring compliance with PCI DSS and rapid patching of vulnerabilities to prevent financial fraud.
Benefits & Limitations
Key Advantages
- Security: Identifies and mitigates vulnerabilities early.
- Compliance: Ensures license adherence, reducing legal risks.
- Automation: Streamlines security checks in CI/CD pipelines.
- Visibility: Provides a comprehensive BoM for transparency.
Common Challenges or Limitations
- False Positives: May flag non-exploitable vulnerabilities, requiring manual review.
- Performance: Scanning large codebases can slow CI/CD pipelines.
- Coverage: Limited by the quality of vulnerability databases.
- Cost: Enterprise SCA tools can be expensive for small teams.
Best Practices & Recommendations
Security Tips
- Regular Scans: Schedule daily or weekly scans to catch new vulnerabilities.
- Policy Enforcement: Define strict policies (e.g., block critical CVEs).
- Patch Management: Prioritize patching based on severity and exploitability.
Performance
- Incremental Scans: Scan only changed code to reduce overhead.
- Caching: Cache vulnerability databases locally to speed up scans.
Maintenance
- Update Tools: Keep SCA tools updated to leverage new features.
- Monitor Dependencies: Use tools like Dependabot for automated updates.
Compliance Alignment
- Align SCA policies with standards like GDPR, HIPAA, or PCI DSS.
- Document BoM for audits.
Automation Ideas
- Integrate SCA with Slack or email for real-time alerts.
- Use webhooks to trigger actions (e.g., auto-create pull requests for fixes).
Comparison with Alternatives
Comparison Table
| Feature | SCA (e.g., Snyk, Black Duck) | SAST (e.g., SonarQube) | DAST (e.g., OWASP ZAP) |
|---|---|---|---|
| Purpose | Analyzes open-source components | Scans custom code for bugs | Tests running applications |
| Focus | Dependencies, licenses | Code quality, vulnerabilities | Runtime vulnerabilities |
| CI/CD Integration | High | High | Moderate |
| Speed | Fast (manifest-based) | Slower (code analysis) | Slow (runtime testing) |
| Use Case | OSS security, compliance | Code quality assurance | Web app security |
When to Choose SCA
- Choose SCA: When using many open-source libraries or containers, or when license compliance is critical.
- Choose SAST: For custom codebases with complex logic.
- Choose DAST: For testing deployed web applications.
Conclusion
SCA is a cornerstone of DevSecOps, enabling teams to secure open-source components, ensure compliance, and maintain robust CI/CD pipelines. As OSS usage grows, SCA’s role will expand, with trends like AI-driven vulnerability prioritization and deeper cloud-native integration on the horizon. To get started, explore tools like Snyk, Black Duck, or Dependabot, and integrate them into your workflows.
Next Steps
- Try a free SCA tool like Snyk or Dependabot.
- Join communities like OWASP or DevSecOps forums on X.