A Modern Security Scanning Blueprint:
The Step-by-Step Checklist for Today’s Software Teams
Security isn’t just about building firewalls—it’s about embedding trust into every phase of your software delivery pipeline. In 2025, high-performing engineering teams know that comprehensive, automated scanning is a must to keep products secure, compliant, and resilient. But what should you actually be scanning—and when?
Here’s your guided tour through a world-class security scanning and monitoring program, broken down phase by phase, complete with the best-in-class tools you can use today.
1. Before You Commit: Security Starts at Your Fingertips
Don’t wait until code is merged to find secrets or vulnerabilities. Modern teams integrate key checks right into the developer’s workflow:
- Secret Detection: Catch passwords and tokens before they ever leave your laptop (try TruffleHog, Gitleaks).
- Code Quality & Linting: Prevent style drift and catch basic bugs early (with ESLint, Pylint).
- Incremental SAST/SCA: Get instant feedback on vulnerabilities in the code or dependencies you just added (SonarLint, Snyk IDE plugins).
2. On Every Commit and Pull Request: Shift Security Left
CI pipelines aren’t just for running tests—they’re your first automated defense layer:
- Static Application Security Testing (SAST): Find code-level security flaws (SonarQube, CodeQL).
- Software Composition Analysis (SCA) & License Compliance: Keep vulnerable or risky open-source packages out of your builds (Snyk, OWASP Dependency-Check).
- Secret Detection (repo-wide): Scan your whole history for exposed secrets (GitGuardian).
- Infrastructure as Code (IaC) Scanning: Secure your cloud configs and deployment manifests (Checkov, TFLint).
- Test Coverage: Measure what’s actually being tested (Jacoco, Coverage.py).
- CI/CD Pipeline Security: Don’t forget the pipeline itself—lock down secrets and plugins (Cider Security, Legit Security).
- Threat Modeling: For new features, proactively look for design risks (Microsoft Threat Modeling Tool).
3. Building and Storing Artifacts: Secure from the Inside Out
Don’t let vulnerabilities sneak into containers or compiled binaries:
- Container Image Scan: Identify vulnerabilities in every OS and app layer (Trivy, Grype, AWS ECR).
- Binary/Artifact Scan: Catch issues in compiled or packaged apps (JFrog Xray, Snyk).
- SBOM Generation: Track every dependency with a Software Bill of Materials (Syft, CycloneDX).
- Supply Chain Security: Ensure build integrity with signed artifacts (in-toto, SLSA, Sigstore).
4. Testing, QA, and Pre-Production: Simulate the Real World
Before going live, put your app through its paces—inside and out:
- DAST (Dynamic Application Security Testing): Launch real attacks on your running app (OWASP ZAP, Burp Suite).
- API Security Testing: Uncover API-specific weaknesses (42Crunch, StackHawk).
- IAST: Instrumented runtime analysis for deep insight (Contrast Security, Veracode).
- Fuzz Testing: Find bugs with random/malformed inputs (AFL, Jazzer, OSS-Fuzz).
- Performance/Load Testing: Test resilience under stress (JMeter, Locust).
5. Production: Continuous Security, Not Just Compliance
Once deployed, your vigilance continues with monitoring and scanning:
- Cloud Security Posture Management (CSPM): Constantly audit your cloud settings (Wiz, Prisma Cloud).
- Cloud Workload Protection Platform (CWPP): Monitor running workloads for threats (Aqua, Sysdig).
- Kubernetes Security: Lock down clusters and monitor for risks (kube-bench, kube-hunter).
- DSPM/DLP: Discover and classify sensitive data (BigID, Varonis, AWS Macie).
- Malware Scanning: Guard against malicious files and runtime exploits (ClamAV, CrowdStrike).
- Network Security Monitoring: Scan for exposed services, ports, and unusual activity (Nessus, Qualys, OSSEC).
- Continuous API Monitoring: Detect risky or anomalous API usage (Salt Security, Noname Security).
- Compliance Auditing: Ensure you meet PCI, HIPAA, SOC2, etc. (AWS Audit Manager, Prisma Cloud).
6. Strategic & Manual Security Practices: The Human Advantage
Automation is powerful—but don’t forget people:
- Threat Modeling: Team-based exercises to foresee and mitigate risks before code is written.
- Manual Code Review: Human eyes on sensitive logic and complex flows.
- Penetration Testing / Red Team: Simulated real-world attacks by skilled professionals.
- Security Awareness Training: Ongoing education to keep everyone sharp.
- Incident Response Exercises: Regular practice for your “fire drills.”
- Metrics & Reporting: Track progress and coverage—what gets measured gets improved.
Wrapping Up: From Checklist to Culture
The best teams use this scanning blueprint not just as a checklist, but as a way to embed security into their engineering DNA. Assign clear owners for each scan, automate wherever you can, and revisit this process often as your tech and threat landscape evolves.
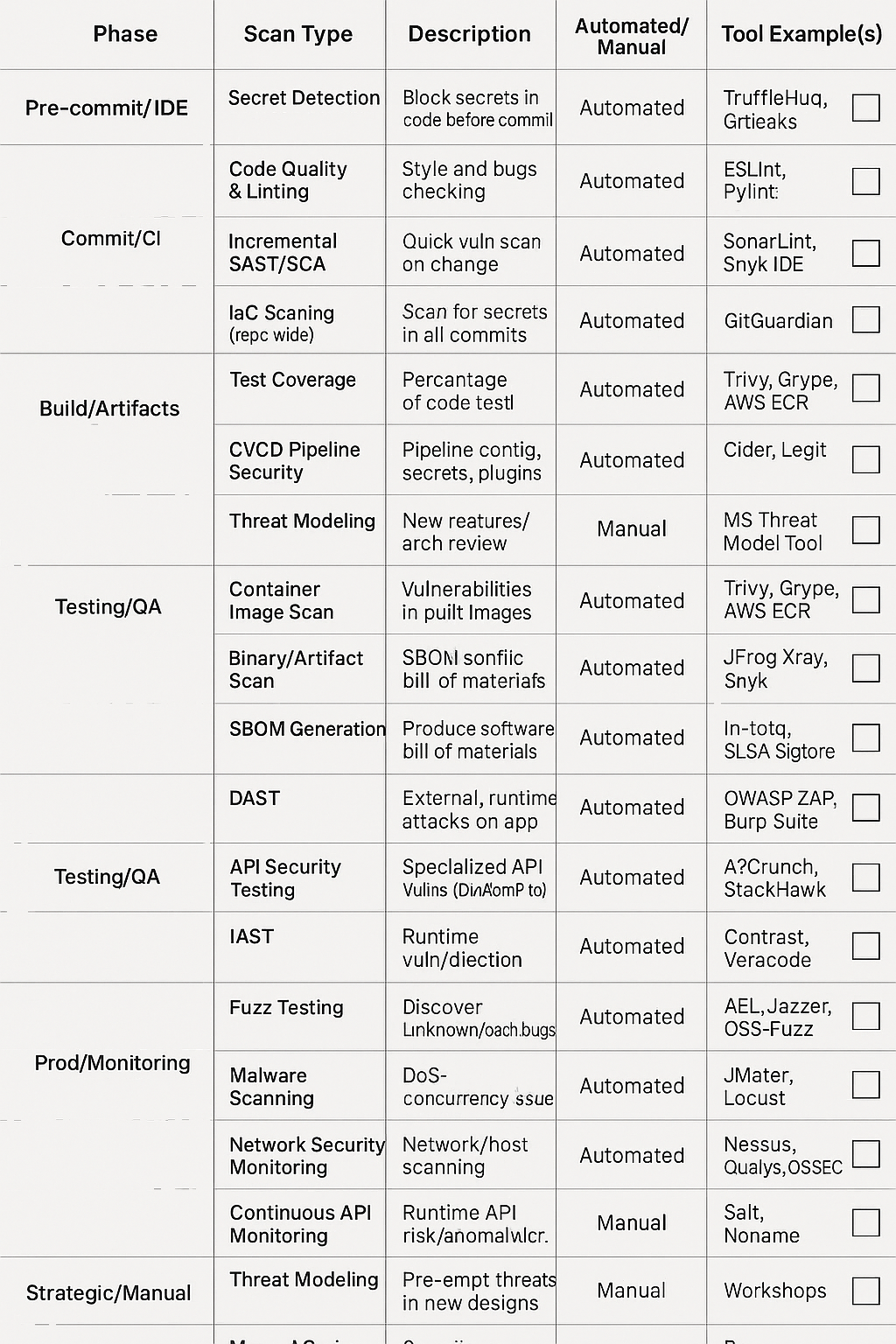
| Phase | Scan Type | Description | Automated/Manual | Tool Example(s) | Status |
|---|---|---|---|---|---|
| Pre-commit/IDE | Secret Detection | Block secrets in code before commit | Automated | TruffleHog, Gitleaks | [ ] |
| Code Quality & Linting | Style and bug checking | Automated | ESLint, Pylint | [ ] | |
| Incremental SAST/SCA | Quick vuln scan on change | Automated | SonarLint, Snyk IDE | [ ] | |
| Commit/CI | SAST | Code-level vulnerabilities | Automated | SonarQube, CodeQL | [ ] |
| SCA & License Compliance | Third-party lib CVEs/licensing | Automated | Snyk, OWASP DC | [ ] | |
| Secret Detection (repo-wide) | Scan for secrets in all commits | Automated | GitGuardian | [ ] | |
| IaC Scanning | Infra config misconfigs | Automated | Checkov, TFLint | [ ] | |
| Test Coverage | Percent of code tested | Automated | Jacoco, Coverage.py | [ ] | |
| CI/CD Pipeline Security | Pipeline config, secrets, plugins | Automated | Cider, Legit | [ ] | |
| Threat Modeling | New features/arch review | Manual | MS Threat Model Tool | [ ] | |
| Build/Artifacts | Container Image Scan | Vulnerabilities in built images | Automated | Trivy, Grype, AWS ECR | [ ] |
| Binary/Artifact Scan | Vulnerabilities in non-container builds | Automated | JFrog Xray, Snyk | [ ] | |
| SBOM Generation | Produce software bill of materials | Automated | Syft, CycloneDX | [ ] | |
| Supply Chain Security | Build provenance, artifact signing | Automated | in-toto, SLSA, Sigstore | [ ] | |
| Testing/QA | DAST | External, runtime attacks on app | Automated | OWASP ZAP, Burp Suite | [ ] |
| API Security Testing | Specialized API vulns (OWASP API Top 10) | Automated | 42Crunch, StackHawk | [ ] | |
| IAST | Runtime vuln detection | Automated | Contrast, Veracode | [ ] | |
| Fuzz Testing | Discover unknown/crash bugs | Automated | AFL, Jazzer, OSS-Fuzz | [ ] | |
| Performance/Load Testing | DoS, concurrency issues | Automated | JMeter, Locust | [ ] | |
| Prod/Monitoring | CSPM | Cloud config and compliance | Automated | Wiz, Prisma Cloud | [ ] |
| CWPP | Runtime protection for workloads | Automated | Aqua, Sysdig, Prisma | [ ] | |
| K8s Security | Cluster, RBAC, runtime | Automated | kube-bench, kube-hunter | [ ] | |
| DSPM/DLP | Sensitive data discovery/classification | Automated | BigID, Varonis, Macie | [ ] | |
| Malware Scanning | File system, container, host malware | Automated | ClamAV, CrowdStrike | [ ] | |
| Network Security Monitoring | Network/host scanning, intrusion | Automated | Nessus, Qualys, OSSEC | [ ] | |
| Continuous API Monitoring | Runtime API risk/anomaly detection | Automated | Salt, Noname | [ ] | |
| Compliance Audit | PCI, HIPAA, SOC2, etc. | Automated | AWS Audit Manager, Prisma | [ ] | |
| Strategic/Manual | Threat Modeling | Pre-empt threats in new designs | Manual | Workshops | [ ] |
| Manual Code Review | Security review of critical logic | Manual | Peer review, checklist | [ ] | |
| Penetration Testing/Red Team | Simulate real attackers | Manual | In-house/third-party | [ ] | |
| Security Awareness Training | Regular training/refreshers | Manual | Phishing drills, eLearning | [ ] | |
| Incident Response Exercises | Tabletop, blue/purple team | Manual | Playbooks | [ ] | |
| Metrics/Reporting | Scan coverage, remediation time, risk trends | Automated/Manual | Dashboards | [ ] |