1. What is Tailscale?
Tailscale is a mesh VPN / software-defined network overlay service that makes it easy to connect devices, services, and networks securely, regardless of where they are located. (Tailscale)
Key points:
- It uses the open-source WireGuard protocol for encrypted point-to‐point tunnels. (Tailscale)
- It allows devices to join a private network (called a “tailnet”) and talk to each other directly, rather than routing all traffic through a central VPN gateway. (Tailscale)
- It is infrastructure‐agnostic: works in cloud, on-premises, IoT, mobile, etc. (Tailscale)
- It integrates identity and access control, meaning access is managed via user identity, device trust, and network policy rather than just IP addresses. (Tailscale)
- The company behind it, Tailscale Inc., was founded in 2019, and the product has grown significantly in the enterprise space. (Wikipedia)
In short: Tailscale = modern VPN/mesh network service+overlay that uses WireGuard under the hood, with identity, access control, and ease-of-use.
2. Use Cases of Tailscale
Tailscale supports a wide variety of use cases—from personal to enterprise. Some of the most common are:
- Business VPN / Remote Access: Provide remote workers, traveling employees, or contractors secure access to internal corporate resources (file shares, internal dashboards, home-grown apps) without the complexity of traditional VPNs. (Tailscale)
- Infrastructure Access: Access cloud VM instances, containers, on-premises servers, Kubernetes clusters, etc., securely from anywhere. (Tailscale)
- Site-to-Site / Multi-Cloud Connectivity: Connect multiple offices, cloud VPCs, regions, or mixed infrastructure in a mesh or hybrid topology without major firewall re-architecture. (Tailscale)
- Developer / Testing Environments: Allow devs to spin up machines/tools anywhere, connect them into a private network, share resources, test services, etc. (Tailscale)
- Zero-Trust Networking & Micro-segmentation: Use identity‐based access controls, device posture, and network policy enforcement to implement least-privilege access to nodes/services. (Tailscale)
- Homelab / Personal Use: For individual users wanting to connect devices (phones, laptops, NAS, IoT) across networks securely and simply. (Tailscale)
These use cases show that Tailscale isn’t simply a “VPN for remote work”—it’s a flexible overlay network that can be used for many connectivity & security patterns.
3. How Tailscale Works
Here’s an explanation of how Tailscale operates, from the underlying technology up to how devices connect, with the latest details.
a) Underlying Protocol & Data Plane
- The data‐plane encryption is built on the WireGuard protocol: each node runs a WireGuard implementation (often wireguard-go) which establishes encrypted tunnels (peer-to-peer). (Tailscale)
- Tailscale intercepts routing on each device: each Tailscale node gets a private IP (e.g., in the 100.x.y.z range) and can connect directly to other nodes in the tailnet if possible. (Liss is More)
- NAT traversal: Tailscale uses techniques to punch through NATs / firewalls; if direct peer‐to‐peer fails, it falls back to relay servers (called DERP – “Designated Encrypted Relay for Packets”). (Tailscale)
b) Control Plane & Coordination
- Tailscale uses a coordination server (control plane) to manage device registration, key distribution (public keys of peers), identity mapping, and policy enforcement. (Tailscale)
- Each device “authenticates” via an identity provider (Google, Microsoft Entra, Okta, etc.) or other SSO/OIDC flow. The identity is mapped to devices and used in ACLs. (Tailscale)
- After a device is approved and joins the tailnet, the coordination server provides it with the public keys, IP addresses and connectivity metadata of other nodes it can talk to (according to policy).
- The coordination server does not sit in the data path for most traffic — once peers know about each other, they attempt direct connections. If direct fails, the relay may be used. This keeps latency low and avoids central bottlenecks. (Tailscale)
c) Routing, Access Control & Topologies
- Each node has a list of “AllowedIPs” (or equivalent) that define which IP ranges/peers it can send to via the Tailscale tunnel.
- Access control: Tailscale supports ACLs (Access Control Lists) that specify which users/devices can access which nodes/ports/protocols. Identity + device posture are used. (Tailscale)
- Topologies: Though meshes are default, you can also set up subnet routers (so a node acts as gateway to a subnet), exit nodes (so all traffic from certain devices routes via one node), and other hybrid patterns. (Tailscale)
d) Workflow Summary
- Install Tailscale client on a device (desktop, server, phone, etc.).
- Authenticate via your identity provider → device registers with the control plane.
- Device receives a unique Tailscale‐internal IP address and appears in the tailnet.
- Device learns of other nodes (public keys, IPs, endpoints) per access policy.
- When Device A wants to talk to Device B:
- It attempts direct UDP (WireGuard) connection to B using known endpoint, key.
- If NAT/traversal fails, traffic relays via DERP.
- Traffic is end-to-end encrypted (WireGuard) between A and B (or via relay).
- Access control: At B’s side, the node checks ACL/policy: is A allowed to connect? If yes, packet is accepted. If no, dropped.
- Optionally: Use exit node, subnet routing, or restrict traffic, run device posture checks, etc.
e) Security & Trust Model
- Every node has a keypair; private key never leaves the device. The public key is shared with approved peers. (Tailscale)
- Identity is used to control access, not just network location (makes this a zero-trust network overlay). (Tailscale)
- No central decryption point: unless traffic is forced via a certain node (exit node), it’s end-to-end encrypted between peers. (Virtualization Review)
4. How Tailscale and WireGuard are Related
The relationship between Tailscale and WireGuard is foundational:
- WireGuard is the underlying VPN protocol used by Tailscale to provide encrypted tunnels. Tailscale relies on WireGuard (and likely the wireguard-go implementation) for its dataplane. (Tailscale)
- Tailscale builds additional layers on top of WireGuard:
- A coordination/control plane (device registration, key distribution, node discovery)
- A NAT traversal/relay fallback mechanism (DERP)
- Identity & ACL integration (so you can use users/groups, not just IPs)
- Easy installer clients across platforms, management UI/console, enterprise features
- In other words:
- WireGuard = secure tunneling engine
- Tailscale = complete solution around WireGuard + management + policy + ease of use
- This means you benefit from WireGuard’s speed, simplicity, and security, while Tailscale gives you the user-friendly overlay, orchestration, and enterprise features.
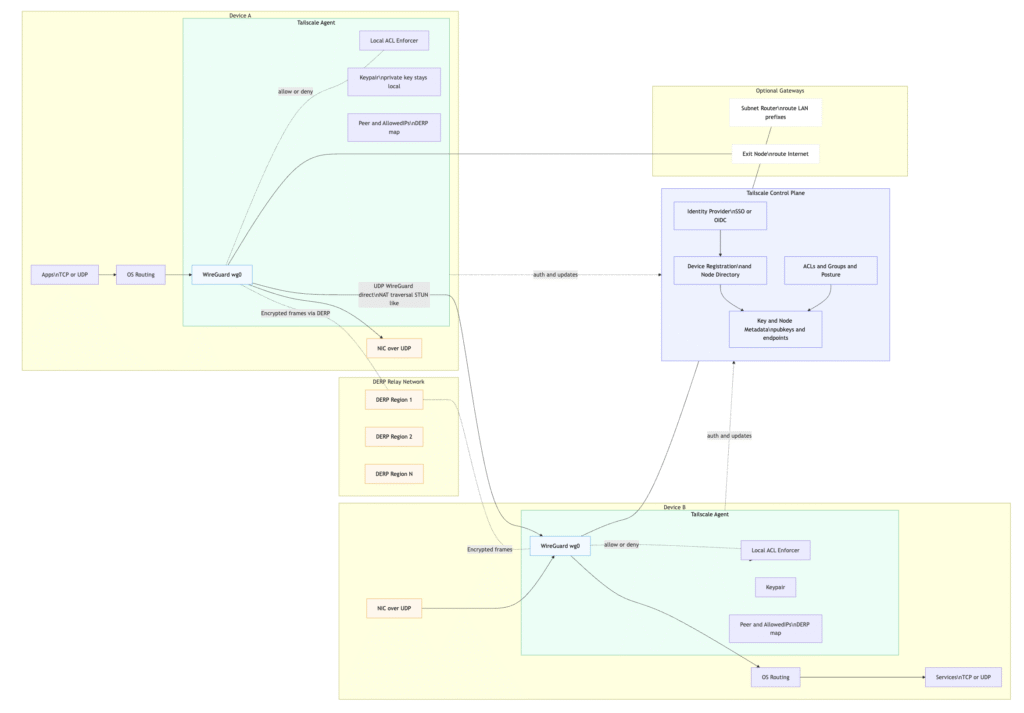
5. Tailscale Architecture (Detailed)
Here is how Tailscale is architected, including major components, flows, and deployment options.
a) Major Components
- Tailscale Client/Agent: Runs on each node (desktop, server, phone, IoT).
- Installs the WireGuard interface (wg0 or equivalent)
- Manages configuration, keypair generation, authorization
- Connects to the control plane
- Handles peer discovery, NAT traversal, DERP fallback
- Control / Coordination Plane: (Hosted by Tailscale or private if self-hosted)
- Handles device registration, identity authentication
- Maintains the list of nodes, public keys, endpoints
- Distributes ACLs/policies to nodes
- Acts as “directory” not heavy traffic router
- DERP Relay Network: Distributed relay servers around the world that devices use when direct peer-to-peer connection fails (due to symmetric NAT, blocked UDP, etc.). (Tailscale)
- Tailnet: The logical network created by your devices. Nodes in your tailnet can talk (subject to ACLs).
- Optional infrastructure components:
- Subnet routers (to make entire subnets reachable)
- Exit nodes (to route internet traffic via a node)
- App connectors (to extend to SaaS or other resources)
- Integration with identity providers (IdPs), device posture, logging/telemetry etc.
b) Deployment Topologies
- Device to Device (Peer-to-Peer Mesh): Default mode—each device connects directly to others when possible.
- Site-to-Site / Multi-Site: Use subnet routers on each network (office, cloud VPC) to connect entire subnets. (Tailscale)
- Exit Node / Remote Access: A device acts as gateway for internet traffic. For example, home desktop becomes exit node for laptop.
- Mixed Cloud + On-Premises: Nodes in different clouds and on-premises join the same tailnet; routing and policy applied uniformly. (Tailscale)
c) Connectivity Flow
- Node boots client → authenticates to control plane via identity.
- Control plane assigns node a tailnet IP, registers its public key, learns endpoint info.
- Client receives list of peers and policies (ACLs).
- When node A wants to reach node B:
- Look up B’s endpoint (public IP:port) via control information.
- Attempt UDP connection (WireGuard handshake) to B.
- If direct fails, use DERP relay to B.
- Once tunnel established (WireGuard) traffic flows encrypted.
- Node B enforces that A’s identity/peer is allowed (via ACLs) before accepting traffic.
- If an exit node or subnet router is used, traffic from A may be routed via another node to reach target.
- Logging, telemetry, and policy enforcement run as part of the overlay.
d) Security / Telemetry / Policy
- ACLs allow specifying who (user, group) can access what (node, port, protocol). (Tailscale)
- Device posture, identity provider integration, and SCIM auto-provisioning for enterprises. (Tailscale)
- Audit logs, network flow logs, and telemetry feed into SIEM or analytics systems. (Tailscale)
- Because each node enforces policy locally, the system avoids a central “choke point” for traffic and avoids single point of failure. (Virtualization Review)
e) Example Reference Architecture (AWS)
For example, deploying Tailscale in AWS may use:
- Agent-to-Agent connectivity: nodes (e.g., EC2) join tailnet directly.
- Subnet router: to expose AWS RDS/private subnet to tailnet. (Tailscale)
- Exit node: for remote users to route traffic through cloud or on-premises node.
✅ Why Use Tailscale (Benefits)
- Rapid deployment: you can join devices to a private network in minutes without complex VPN infrastructure. (Tailscale)
- Low latency / high performance: because of direct peer connectivity and minimal central routing. (Tailscale)
- Identity-based access, zero-trust networking: you control access by user/device identity, not just network address. (Tailscale)
- Infrastructure‐agnostic: works across cloud, on-prem, mobile, IoT, etc. (Tailscale)
- Flexible network topology and segmentation: mesh, hubs, subnets, exit nodes—all possible.
- Security features for enterprises: ACLs, device posture, audit logs, SIEM integration, etc.
- Open source at its core, and built on WireGuard, so benefits from modern cryptography and auditability. (Tailscale)
⚠️ Considerations & Limitations
- While traffic is peer-to-peer by default, certain environments (e.g., corporate NATs blocking UDP) may need relay fallback or extra setup.
- Some advanced enterprise needs (very large scale, custom routing, regulatory constraints) may still require additional design.
- Because of the control plane involvement (though not in the data path), some organizations may evaluate trust and governance of the service.
- Though the free and paid tiers exist, enterprise features will incur cost, and careful policy design is required.
flowchart LR
%% ================================
%% TAILSCALE: ARCHITECTURE OVERVIEW
%% ================================
%% ------- Tailnet Devices (Data Plane) -------
subgraph DEV1["Device A"]
A_App["Apps\nTCP or UDP"]
A_RT["OS Routing"]
subgraph A_Agent["Tailscale Agent"]
A_WG["WireGuard wg0"]
A_ACL["Local ACL Enforcer"]
A_KP["Keypair\nprivate key stays local"]
A_CFG["Peer and AllowedIPs\nDERP map"]
end
A_NIC["NIC over UDP"]
end
subgraph DEV2["Device B"]
B_App["Services\nTCP or UDP"]
B_RT["OS Routing"]
subgraph B_Agent["Tailscale Agent"]
B_WG["WireGuard wg0"]
B_ACL["Local ACL Enforcer"]
B_KP["Keypair"]
B_CFG["Peer and AllowedIPs\nDERP map"]
end
B_NIC["NIC over UDP"]
end
%% ------- Control Plane (Out of band) -------
subgraph CTRL["Tailscale Control Plane"]
IdP["Identity Provider\nSSO or OIDC"]
Reg["Device Registration\nand Node Directory"]
Keys["Key and Node Metadata\npubkeys and endpoints"]
Policy["ACLs and Groups and Posture"]
end
IdP --> Reg
Reg --> Keys
Policy --> Keys
%% ------- DERP Relay Fabric (fallback) -------
subgraph DERP["DERP Relay Network"]
D1["DERP Region 1"]
D2["DERP Region 2"]
D3["DERP Region N"]
end
%% ------- Enrollment / Updates (Control plane traffic) -------
A_Agent -. "auth and updates" .-> CTRL
B_Agent -. "auth and updates" .-> CTRL
%% ------- Data Plane: Direct P2P (preferred) -------
A_WG -- "UDP WireGuard direct\nNAT traversal STUN like" --> B_WG
%% ------- Data Plane: Relay (when direct fails) -------
A_WG -. "Encrypted frames via DERP" .- D1
D1 -. "Encrypted frames" .- B_WG
%% ------- Local Enforcement & Routing -------
A_App --> A_RT --> A_WG
A_Agent --> A_ACL
A_ACL -. "allow or deny" .- A_WG
A_WG --> A_NIC
B_NIC --> B_WG
B_WG -. "allow or deny" .- B_ACL
B_ACL --> B_Agent
B_WG --> B_RT --> B_App
%% ------- Optional Topologies -------
subgraph NETX["Optional Gateways"]
SubnetR["Subnet Router\nroute LAN prefixes"]
ExitNode["Exit Node\nroute Internet"]
end
B_WG --- SubnetR
A_WG --- ExitNode
%% ------- Styling -------
classDef agent fill:#e8fff5,stroke:#10b981,color:#111;
classDef wg fill:#f0f9ff,stroke:#0ea5e9,color:#111;
classDef plane fill:#fff7ed,stroke:#f59e0b,color:#111;
classDef ctrl fill:#eef2ff,stroke:#6366f1,color:#111;
classDef note fill:#ffffff,stroke:#d1d5db,stroke-dasharray:3 3,color:#111;
class A_Agent,B_Agent agent
class A_WG,B_WG wg
class A_NIC,B_NIC plane
class CTRL,IdP,Reg,Keys,Policy ctrl
class D1,D2,D3 plane
class SubnetR,ExitNode note