Introduction & Overview
Syslog is a standard protocol for message logging, widely used in IT systems to collect, store, and analyze log data from various sources. In the context of DevSecOps, Syslog plays a critical role in enhancing visibility, ensuring security, and maintaining compliance across the software development lifecycle. This tutorial provides an in-depth exploration of Syslog, its architecture, setup, use cases, benefits, limitations, and best practices, tailored for technical practitioners in DevSecOps.
What is Syslog?
Syslog (System Logging Protocol) is a standard protocol defined in RFC 5424 for sending, receiving, and storing log messages across networked systems. It enables centralized logging, allowing administrators to monitor system activities, detect anomalies, and troubleshoot issues efficiently.
History or Background
Syslog was introduced in the 1980s by Eric Allman as part of the Sendmail project. It evolved into a standardized protocol, with RFC 3164 (2001) and RFC 5424 (2009) defining its modern structure. Today, Syslog is integral to system administration, security monitoring, and DevSecOps workflows.
Why is it Relevant in DevSecOps?
In DevSecOps, where security is integrated into development and operations, Syslog provides:
- Visibility: Centralized logs offer insights into application and infrastructure behavior.
- Security: Logs help detect threats, track unauthorized access, and support incident response.
- Compliance: Syslog ensures audit trails for regulatory requirements (e.g., GDPR, HIPAA).
- Automation: Logs integrate with CI/CD pipelines for automated monitoring and alerting.
Core Concepts & Terminology
Key Terms and Definitions
- Facility: Categories of log sources (e.g.,
kern,auth,syslog). - Severity: Levels of log message importance (e.g.,
emergency,alert,debug). - Message: The log entry containing timestamp, hostname, and content.
- Syslog Daemon: Software (e.g.,
rsyslog,syslog-ng) that processes logs. - Transport: Protocols like UDP, TCP, or TLS for log transmission.
| Term | Definition |
|---|---|
| Syslog Server | Centralized system that receives and stores logs. |
| Syslog Client | Device or application that sends logs to the server. |
| Facility | Log source category (e.g., auth, cron, daemon). |
| Severity | Log level indicating urgency (e.g., info, warning, error). |
| Message | The actual log content (event details). |
| RFC 5424 | Defines syslog message format and protocol. |
How It Fits into the DevSecOps Lifecycle
Syslog integrates into DevSecOps at multiple stages:
- Plan: Logs inform security policies and compliance requirements.
- Develop: Application logs feed into Syslog for debugging and monitoring.
- Test: Logs validate security controls and detect vulnerabilities.
- Deploy: Syslog tracks deployment events and CI/CD pipeline activities.
- Operate: Centralized logs enable real-time monitoring and incident response.
| DevSecOps Phase | Role of Syslog |
|---|---|
| Plan | Define compliance logging requirements. |
| Develop | Integrate structured logging in code. |
| Build | Monitor build logs for anomalies. |
| Test | Capture and analyze test results. |
| Release | Log deployment activity and errors. |
| Operate | Monitor production environment, detect threats. |
| Monitor | Aggregate logs for dashboards, alerting. |
Architecture & How It Works
Components and Internal Workflow
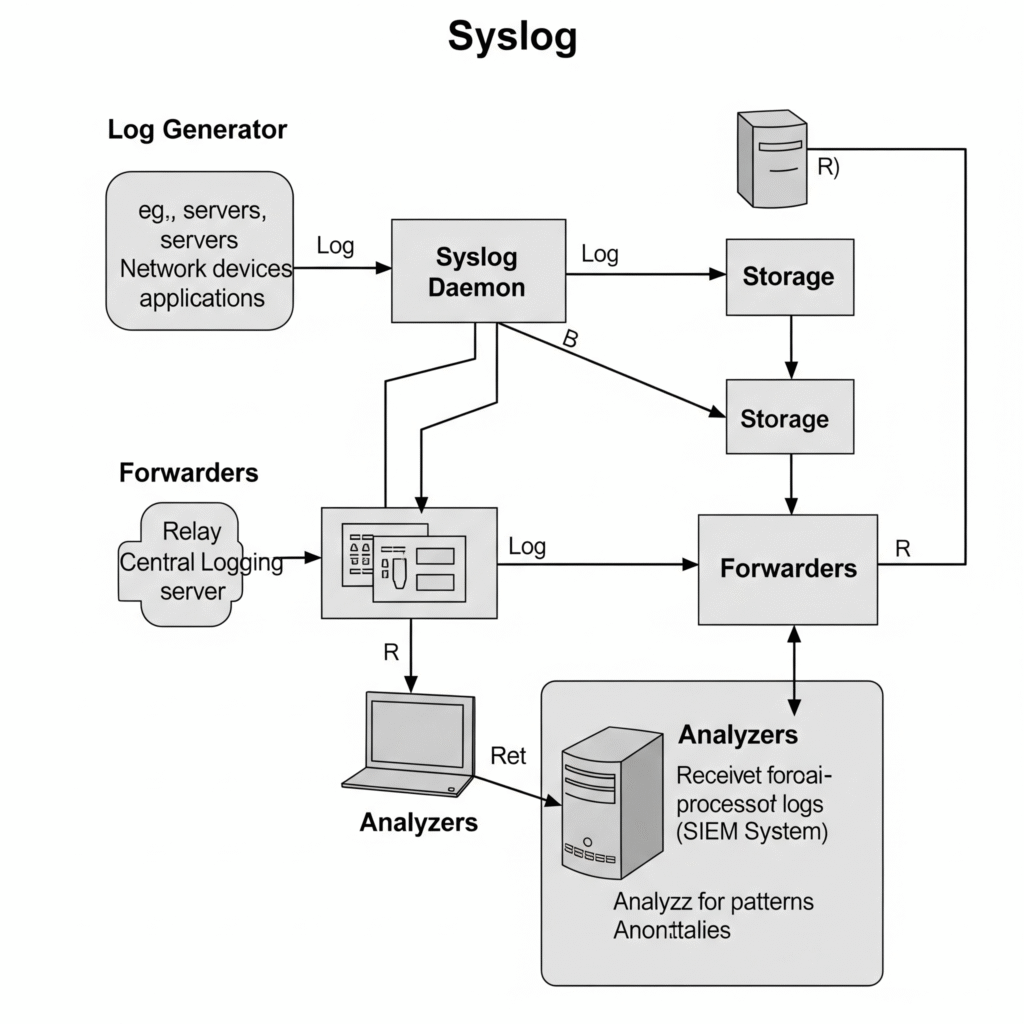
Syslog operates through:
- Log Generators: Devices or applications producing logs (e.g., servers, firewalls).
- Syslog Daemon: Collects and processes logs (e.g.,
rsyslog,syslog-ng). - Storage: Logs are stored locally or in centralized databases (e.g., Elasticsearch).
- Forwarders: Relay logs to other systems or SIEM tools.
- Analyzers: Tools like Splunk or ELK Stack process logs for insights.
Workflow: Applications send logs to a Syslog daemon via UDP/TCP. The daemon filters, processes, and forwards logs based on configuration.
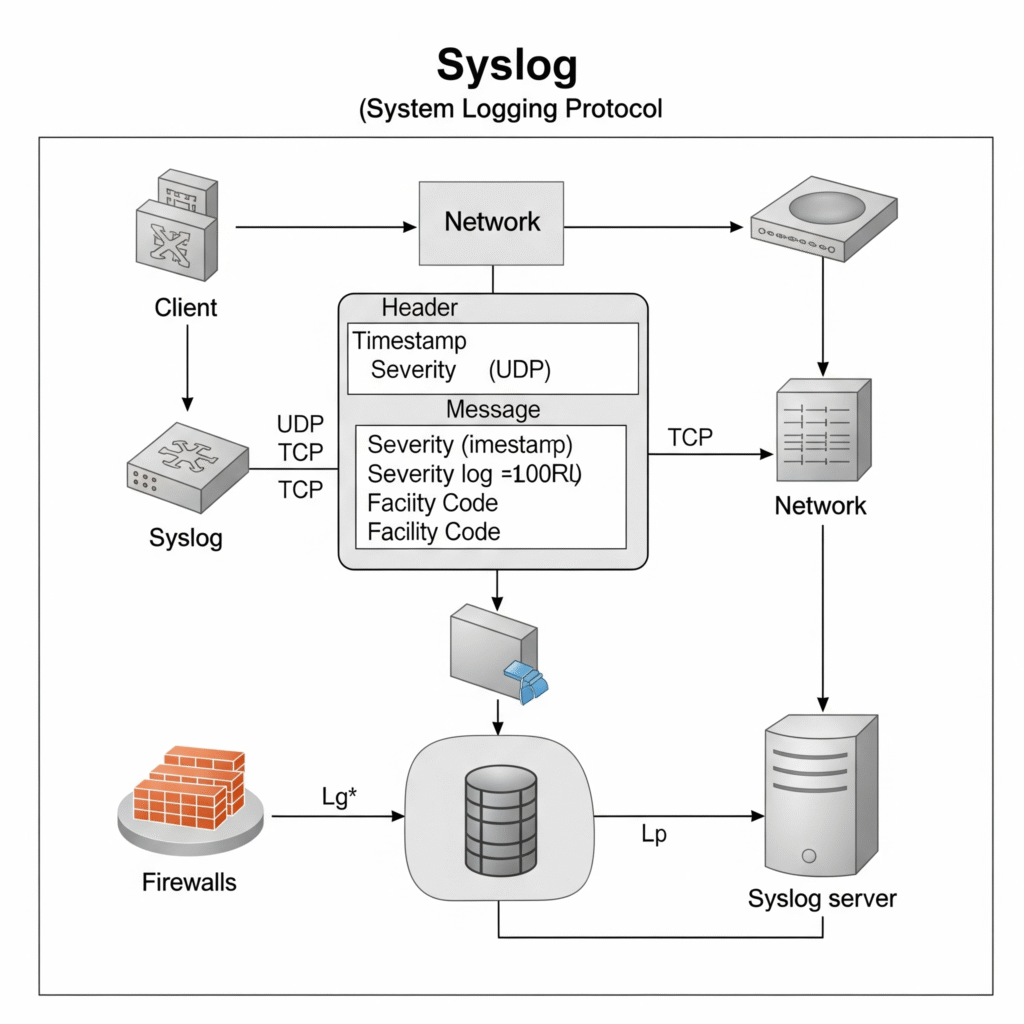
Architecture Diagram
Imagine a diagram with:
- Left: Applications and devices sending logs.
- Center: Syslog daemon (
rsyslog) receiving and processing logs. - Right: Logs stored in a database or forwarded to a SIEM (e.g., Splunk).
- Arrows: Indicate log flow over UDP/TCP/TLS.
[Application/Device] --Syslog Message--> [Syslog Server (e.g., rsyslog)]
| |
+--> [Parser/Filter] --> [Storage Backend] --> [SIEM/Dashboard]
Integration Points with CI/CD or Cloud Tools
- CI/CD: Syslog captures pipeline logs from Jenkins, GitLab CI, or GitHub Actions.
- Cloud: Integrates with AWS CloudWatch, Azure Monitor, or GCP Logging.
- SIEM: Feeds logs to Splunk, Elastic, or QRadar for security analysis.
Installation & Getting Started
Basic Setup or Prerequisites
- Linux system (e.g., Ubuntu 20.04 or CentOS 8).
- Root or sudo access.
- Network connectivity for remote logging.
- Optional: TLS certificates for secure transmission.
Hands-On: Step-by-Step Setup Guide
This guide sets up rsyslog on Ubuntu 20.04 for local and remote logging.
- Install rsyslog:
sudo apt update
sudo apt install rsyslog- Configure rsyslog: Edit
/etc/rsyslog.conf:
# Enable UDP/TCP
module(load="imudp")
input(type="imudp" port="514")
module(load="imtcp")
input(type="imtcp" port="514")
# Log to file
*.* /var/log/syslog- Forward logs to a remote server: Add to
/etc/rsyslog.conf:
*.* @remote-server:514 # UDP
*.* @@remote-server:514 # TCP- Restart rsyslog:
sudo systemctl restart rsyslog- Verify logs: Check
/var/log/syslogor use:
logger "Test message to syslog"Real-World Use Cases
Scenario 1: CI/CD Pipeline Monitoring
A DevSecOps team uses Syslog to collect logs from a Jenkins pipeline. Logs track build failures, security scans, and deployment events, feeding into Splunk for analysis.
Scenario 2: Intrusion Detection
A financial institution uses Syslog to centralize firewall and application logs. Anomalous login attempts trigger alerts via a SIEM, enabling rapid response.
Scenario 3: Compliance Auditing
A healthcare provider uses Syslog to store access logs for HIPAA compliance. Logs are archived and audited to ensure patient data security.
Industry-Specific Example: E-Commerce
An e-commerce platform logs user transactions and API calls via Syslog, integrating with AWS CloudWatch to detect fraudulent activities in real time.
Benefits & Limitations
Key Advantages
- Centralized logging simplifies monitoring.
- Lightweight and widely supported across platforms.
- Flexible transport options (UDP, TCP, TLS).
- Integrates with modern DevSecOps tools (SIEM, cloud platforms).
Common Challenges or Limitations
- UDP-based logging is unreliable (potential message loss).
- Limited message structure compared to JSON-based logging.
- Scalability issues with high log volumes.
- Security risks if TLS is not configured.
| Limitation | Description |
|---|---|
| Unencrypted by default | Use TLS for secure transmission. |
| Basic log structure | No schema, hard to parse unless formatted. |
| Limited storage | Needs external tools for retention/archiving. |
| No built-in visualization | Must integrate with tools like ELK. |
Best Practices & Recommendations
Security Tips
- Use TLS for secure log transmission.
- Restrict Syslog server access with firewalls.
- Regularly rotate and archive logs.
Performance and Maintenance
- Optimize filters to reduce log noise.
- Use high-performance daemons like
syslog-ngfor large-scale setups. - Monitor disk space for log storage.
Compliance Alignment and Automation
- Map Syslog facilities to compliance requirements (e.g.,
authfor access logs). - Automate log analysis with scripts or SIEM rules.
- Use CI/CD plugins to push pipeline logs to Syslog.
Comparison with Alternatives
| Feature | Syslog | Fluentd | Logstash |
|---|---|---|---|
| Protocol | UDP/TCP/TLS | JSON-based | JSON-based |
| Ease of Setup | Simple | Moderate | Complex |
| Scalability | Moderate | High | High |
| Integration | Broad (SIEM, Cloud) | Cloud-native | Elastic Stack |
| Resource Usage | Low | Moderate | High |
When to Choose Syslog
- Small to medium-sized environments needing lightweight logging.
- Legacy systems with native Syslog support.
- Scenarios requiring broad compatibility over structured logging.
Conclusion
Syslog remains a cornerstone of logging in DevSecOps, offering simplicity, flexibility, and integration with modern tools. As organizations adopt cloud-native and microservices architectures, Syslog’s role may evolve with structured logging formats. Future trends include tighter integration with AI-driven log analysis and cloud platforms.